

Skyhigh Securityは、クラウド、ウェブ、データ、ネットワークセキュリティのニーズに対応しながら、リモートワークの実現を可能にします。
強力な
ゼロトラストセキュリティスイート製品群

Cloud Access Security Broker
クラウドアプリの完全な可視化と制御を実現し、リアルタイムのデータ保護と脅威防止を実現するマルチテナント型CASBソリューションです。

Secure Web Gateway
ゼロデイ攻撃から従業員を保護し、ウェブやクラウドアプリケーションにアクセスする際のデータ保護を強化する明晰で成熟したウェブセキュリティソリューションです。

Private Access(ZTNA)
リモートワークや拡張されたワークフォースを保護する代替VPNソリューションで、管理下および非管理下のデバイスからプライベートアプリケーションに安全にアクセスすることができます。

Cloud-Native Application Protection Platform
業界初の包括的で自動化された摩擦のないプラットフォームで、企業のクラウドネイティブアプリケーションエコシステムを保護します。
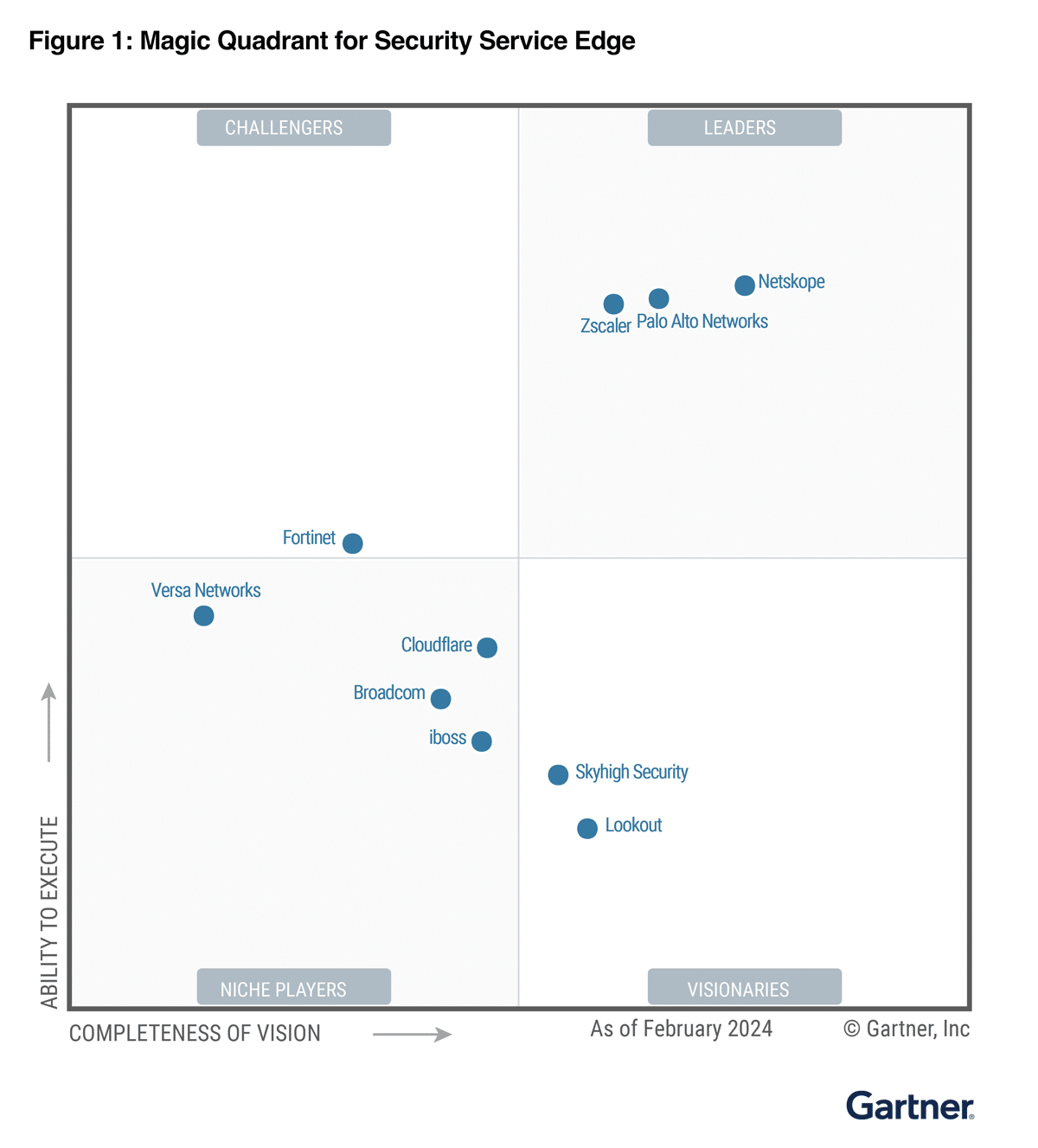
Skyhigh Security 2024年ガートナー®マジック・クアドラント™のSecurity Service Edge (SSE)において、2年連続でビジョナリーに選出。
レポートを読むSkyhigh Security は、ビジョンの完全性と実行力が評価されている。
最も堅牢で、統合されたものを紹介する
クラウドセキュリティプラットフォームを利用可能
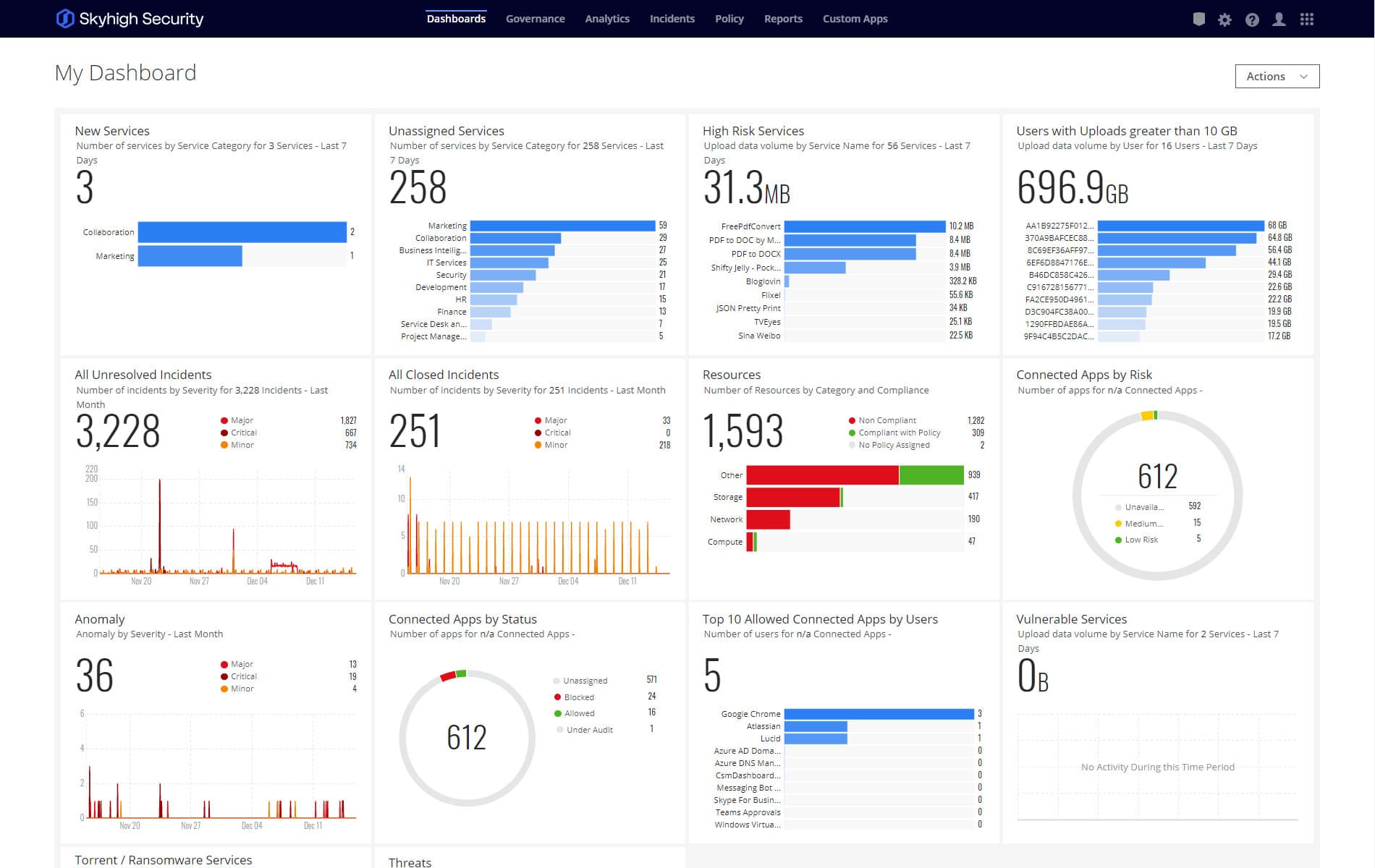
SSEの全製品にDLPとRBIを標準装備しており、単一の強力なプラットフォームに完全に統合されています。
プラットフォーム詳細
受賞歴
賞や表彰
クラウドの安全性を確保するための次のステップ
- 全方位でのデータ保護
- 拡張性の高いService Edge
- 高度な脅威保護
完全な統合プラットフォームで、全てを単一コンソールから管理します





