Articles by Author

Privacy & Identity Protection
What is the Cloud?
You’ve probably heard of people storing information in “the cloud,” but what does that really mean, and...May 25, 2015 | 3 MIN READ
McAfee Labs
Malware Spreads Through Facebook Tag Scam
McAfee has recently observed a malware spreading through Facebook. This type of malware is not new, but...May 18, 2015 | 4 MIN READ

McAfee News
Moore’s Law and Security
We in the technology industry owe a lot to Moore’s Law, as it’s given us the foundation...May 06, 2015 | 3 MIN READ

Privacy & Identity Protection
What is Shoulder Surfing?
The next time you’re in a public place and glued to your smartphone or tablet — whether...May 04, 2015 | 3 MIN READ

Mobile Security
Millennials Choose Convenience Over Security When it Comes to Information Sharing
For better or for worse, we’ve ended up amidst a society built on information sharing. There are...Apr 28, 2015 | 4 MIN READ
Privacy & Identity Protection
What is Spam?
Everyone’s heard of spam as it pertains to emails. Spam isn’t necessarily a malicious message designed to...Apr 27, 2015 | 3 MIN READ

Privacy & Identity Protection
Importance of Renewing Your Security Software on a Regular Basis – Part II
Let’s start by refreshing all that we discovered in my previous blog, where I was telling Reena...Apr 22, 2015 | 3 MIN READ

Family Safety
6 Tips for Protecting Your Social Media Accounts
10 years ago, many of us were hearing about social media for the first time. Now, social...Apr 20, 2015 | 3 MIN READ

Mobile Security
‘Secret Chat’ Messages Aren’t So Secret After All
The universal truth about secrets? They almost always tend to get leaked. This was the case for...Apr 14, 2015 | 3 MIN READ
McAfee Labs
VaultCrypt Ransomware Hides Its Traces While Stealing Web Credentials
A recent ransomware variant of Vaultcrypt both tidies up after itself and steals the victim's web page login data.Apr 13, 2015 | 4 MIN READ

Privacy & Identity Protection
What is a Virus?
Have you ever had the chicken pox? This common childhood illness has another name—the varicella zoster virus....Apr 13, 2015 | 3 MIN READ
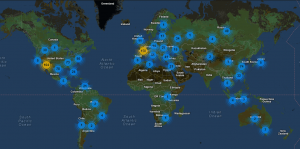
Internet Security
Here’s What You Need To Know About Botnets
In the year of 2000, Professor Vijay Pande, a renowned Stanford University researcher, released a little program...Apr 09, 2015 | 4 MIN READ