Authored by Dexter Shin
McAfee’s Mobile Research Team discovered a new and active Android malware campaign targeting Bengali-speaking users, mainly Bangladeshi people living abroad. The app poses as popular financial services like TapTap Send and AlimaPay. It is distributed through phishing sites and FacebookFacekbook pages, and the app steals users’ personal and financial information. The campaign remains highly active, with the command-and-control (C2) server operational and connected to multiple evolving domains. While the attack techniques are not new, the campaign’s cultural targeting and sustained activity reflect how cybercriminals continue to adapt their strategies to reach specific communities. McAfee Mobile Security already detects this threat as Android/FakeApp. For more information, visit McAfee Mobile Security.
Bangladeshi people living abroad, particularly in countries such as Saudi Arabia, the UAE, Malaysia, and the UK, rely heavily on mobile money services to send remittances and verify their identities for various purposes. Services like bKash, TapTap Send, and AlimaPay are widely used and trusted within this community.
In 2024, annual remittances sent to Bangladesh reached nearly $26.6 billion, ranking sixth globally and third in South Asia. This massive flow of cross-border funds highlights the economic importance and digital engagement of the Bangladeshi diaspora.
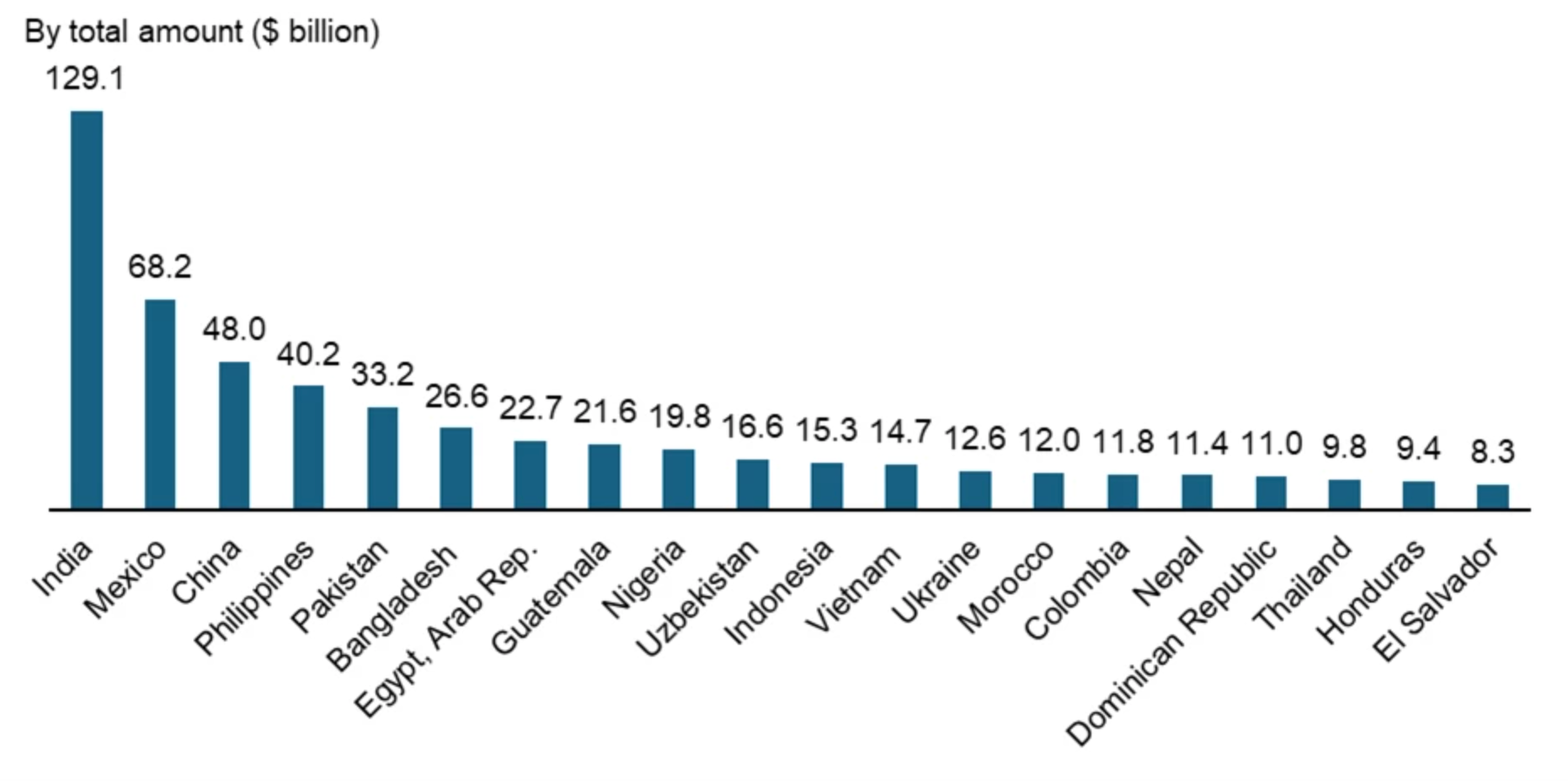
Figure 1. Top Recipients of Remittances in 2024 (Source: World Bank)
As more people use mobile financial apps, cybercriminals are finding new ways to trick them using fake apps and phishing websites. Many users trust apps shared by friends or family, and some may not know how to spot scams. This makes them easy targets for attackers.
In May 2025, McAfee’s Mobile Research Team identified a malware campaign designed to exploit these conditions. The fake Android app impersonates well-known money transfer services and steals personal information such as the user’s name, email address, phone number, and photo ID (such as a passport or national ID card). It also attempts to collect financial data like card numbers through fake in-app pages. Moreover, the C2 server’s storage is publicly exposed, meaning that the stolen data can be accessed by anyone, which significantly increases the risk of abuse.
Technical Findings
Distribution Methods
Over the past few weeks, these fake apps have continued to appear, suggesting an active and sustained campaign targeting Bengali-speaking users. These apps are primarily distributed through phishing websites that mimic trusted remittance services, often shared via fake Facebook pages.
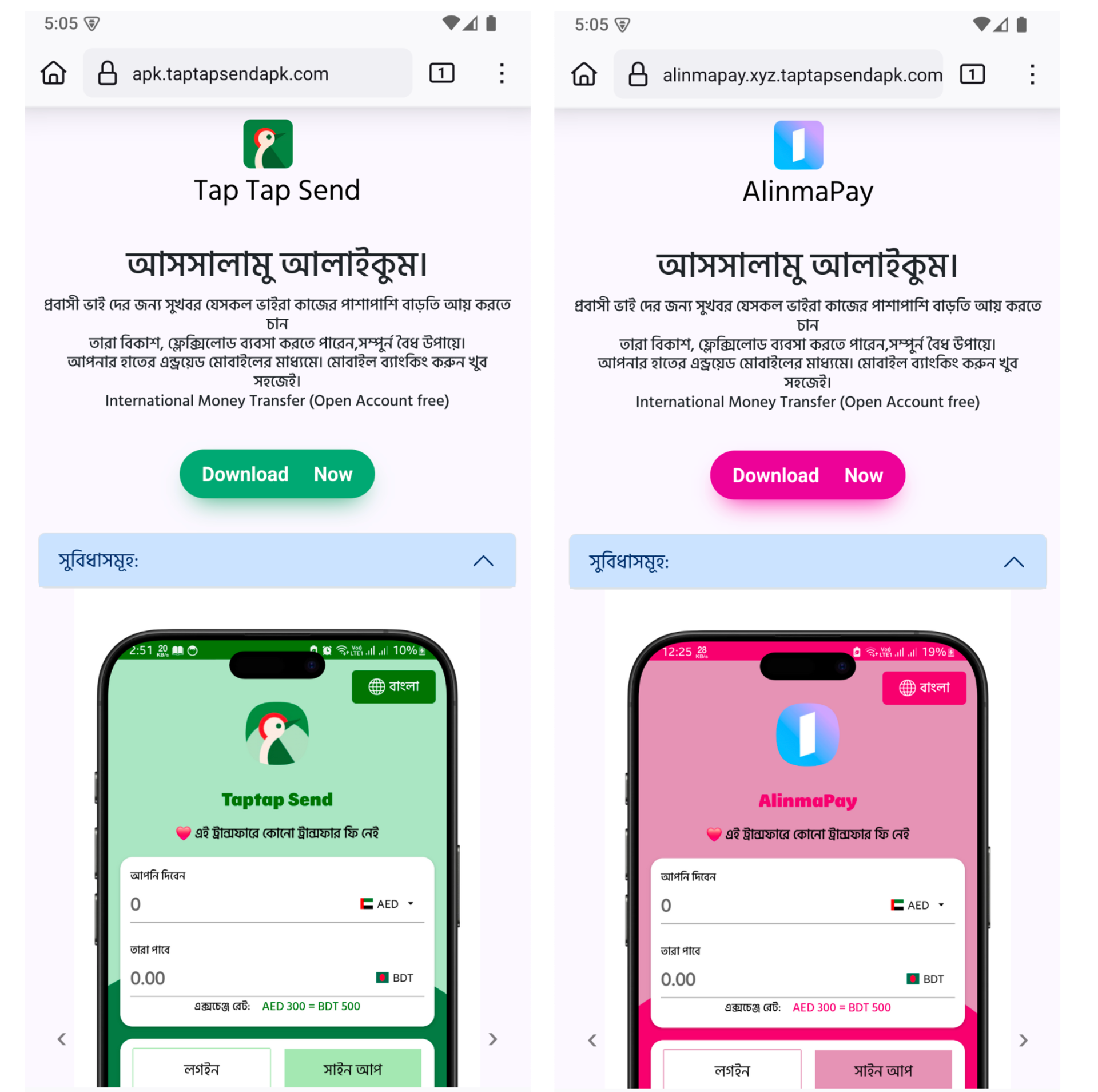
Figure 2. Screenshot of a phishing website
The page is written entirely in Bengali, mimicking a legitimate remittance service commonly used by Bangladeshi expatriates. Below is a translated excerpt of the main message shown on the landing page:
Bengali (original):
আসসালামু আলাইকুম।
প্রবাসী ভাইদের জন্য সুখবর। যারা কাজের পাশাপাশি বাড়তি আয় করতে চান, তারা বিকাশ, ফ্ল্যাশলোড ব্যবসা করতে পারেন। সম্পূর্ণ বৈধ উপায়ে। আপনার হাতের মধ্যে রয়েছে মোবাইলের মাধ্যমে। মোবাইল ব্যাংকিং করুন খুব সহজেই।
English (translation):
Peace be upon you.
Good news for our brothers living abroad. If you’re looking to earn extra income along with your job, you can do business with bKash or FlashLoad in a completely legal way. Everything is within your reach through mobile. Mobile banking is very easy.
In addition to phishing websites, the attackers also created fake Facebook pages that closely resemble legitimate remittance services. These pages often reuse official logos, promotional images, and even videos taken from real financial platforms to appear trustworthy. However, the site links on these pages point to phishing websites hosting the malicious app.
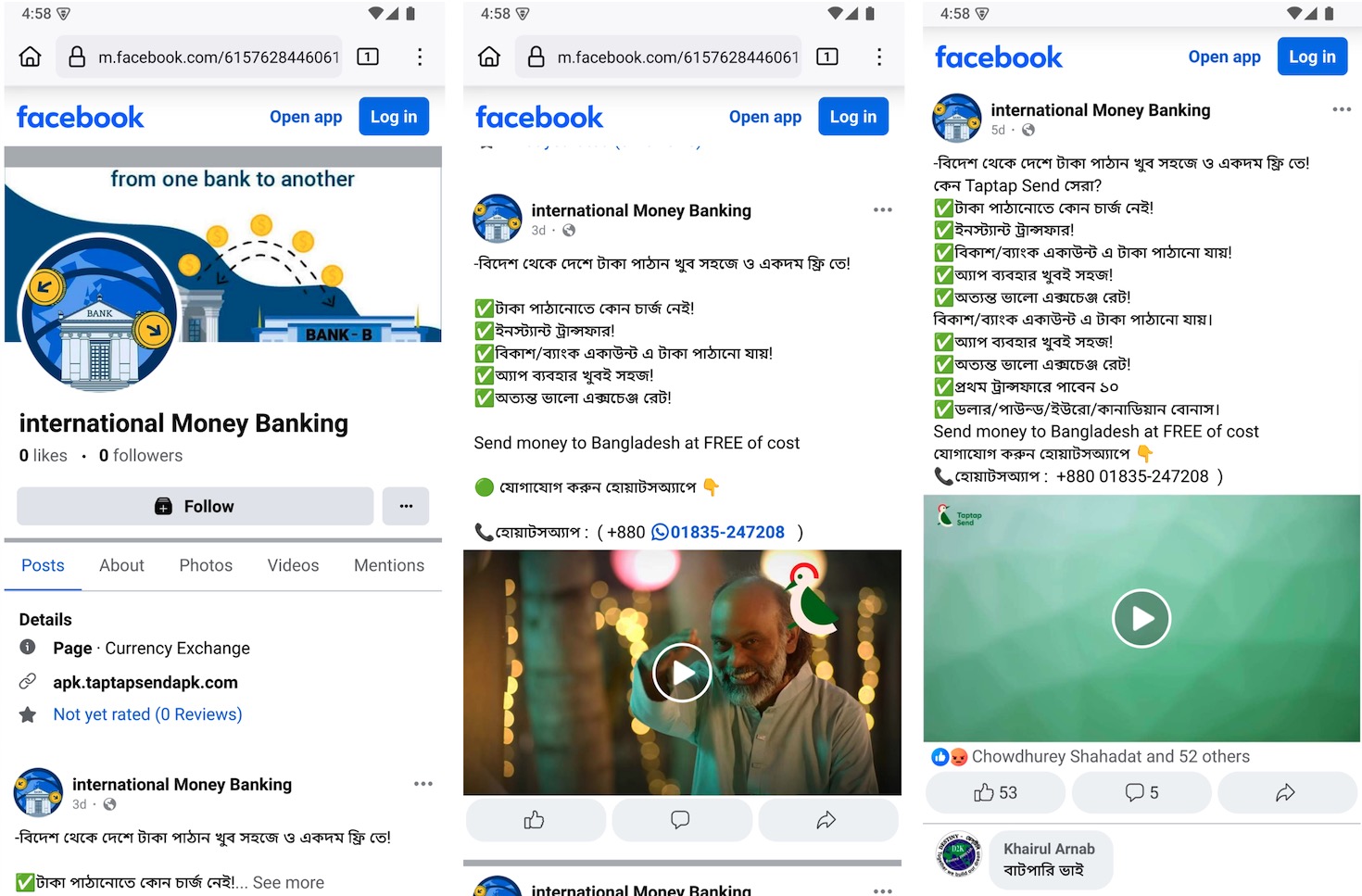
Figure 3. Fake Facebook page mimicking a legitimate remittance service
Fake App Analysis
Once installed, the fake app immediately presents an interface that closely resembles a legitimate remittance application. It supports both Bengali and English language options and shows realistic-looking exchange rates.
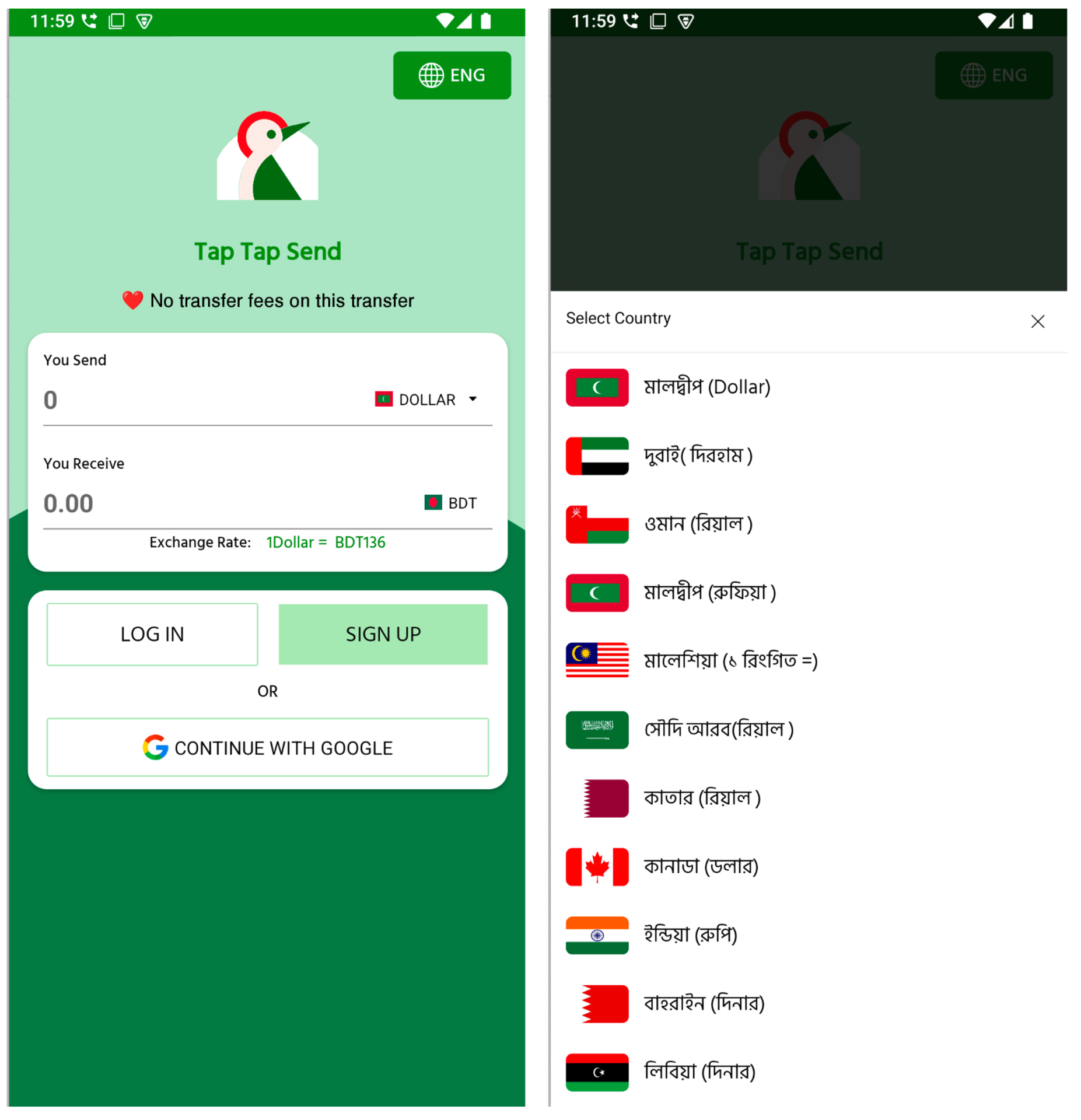
Figure 4. Initial UI of the fake TapTap Send app
Users can select from a list of countries with large Bangladeshi expatriate populations, such as Maldives, Dubai, Oman, Saudi Arabia, Malaysia, Canada, and India, to simulate money transfers to Bangladeshi Taka (BDT). These details are likely included to establish trust and make the app appear functional. However, these screens serve as bait to encourage users to proceed with account creation and enter personal information. As users continue through the registration flow, the app requests increasingly sensitive data in multiple stages. First, it requests the user’s email address and full name. Then, it prompts them to select their country of residence and provide a valid mobile number. Next, users are asked to choose an account type, either “Personal” or “Agent”, a distinction commonly seen in real remittance platforms.
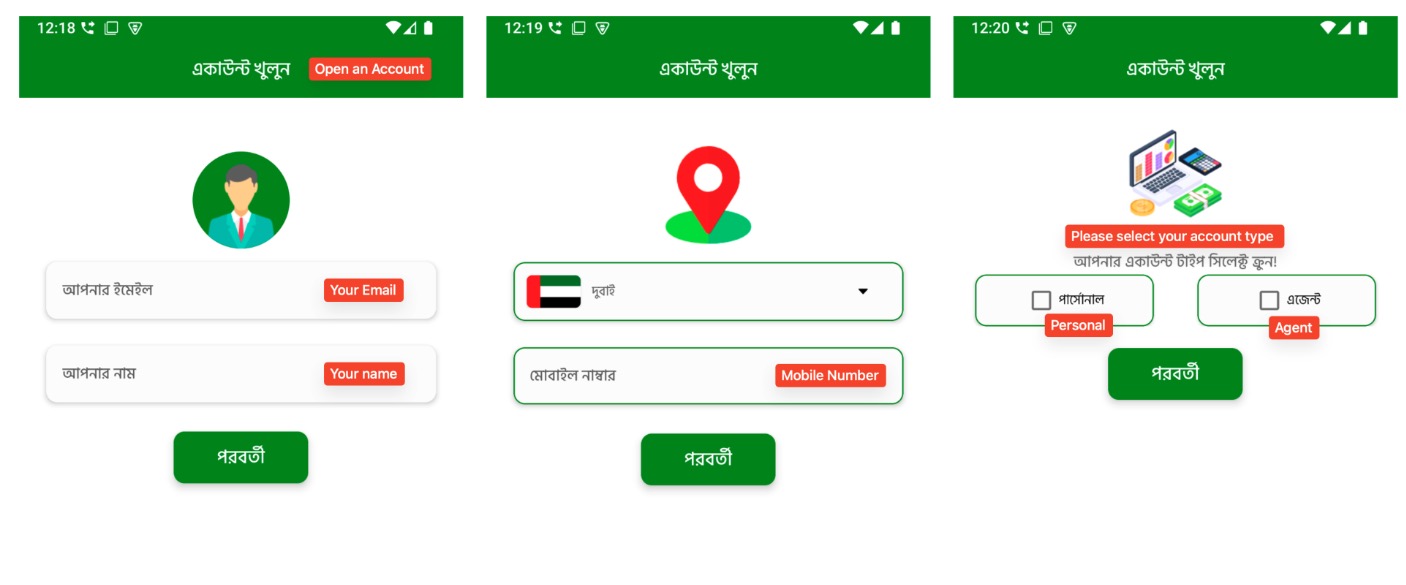
Figure 5. Multi-step registration flow (1)
Following this, the app reaches its most sensitive stage: it asks the user to take and upload a photo of an official ID, such as a passport, national ID (NID), or an e-commerce verification photo. This request is made in the local language and framed as a requirement to complete account setup. After uploading the ID, users are then asked to create a login password and a 5-digit PIN, just like real financial apps. This step makes the app feel more trustworthy and secure, but the collected credentials could later be used in credential stuffing attacks. All of this information is sent to the C2 server and stored, making it available for future fraud or identity theft.
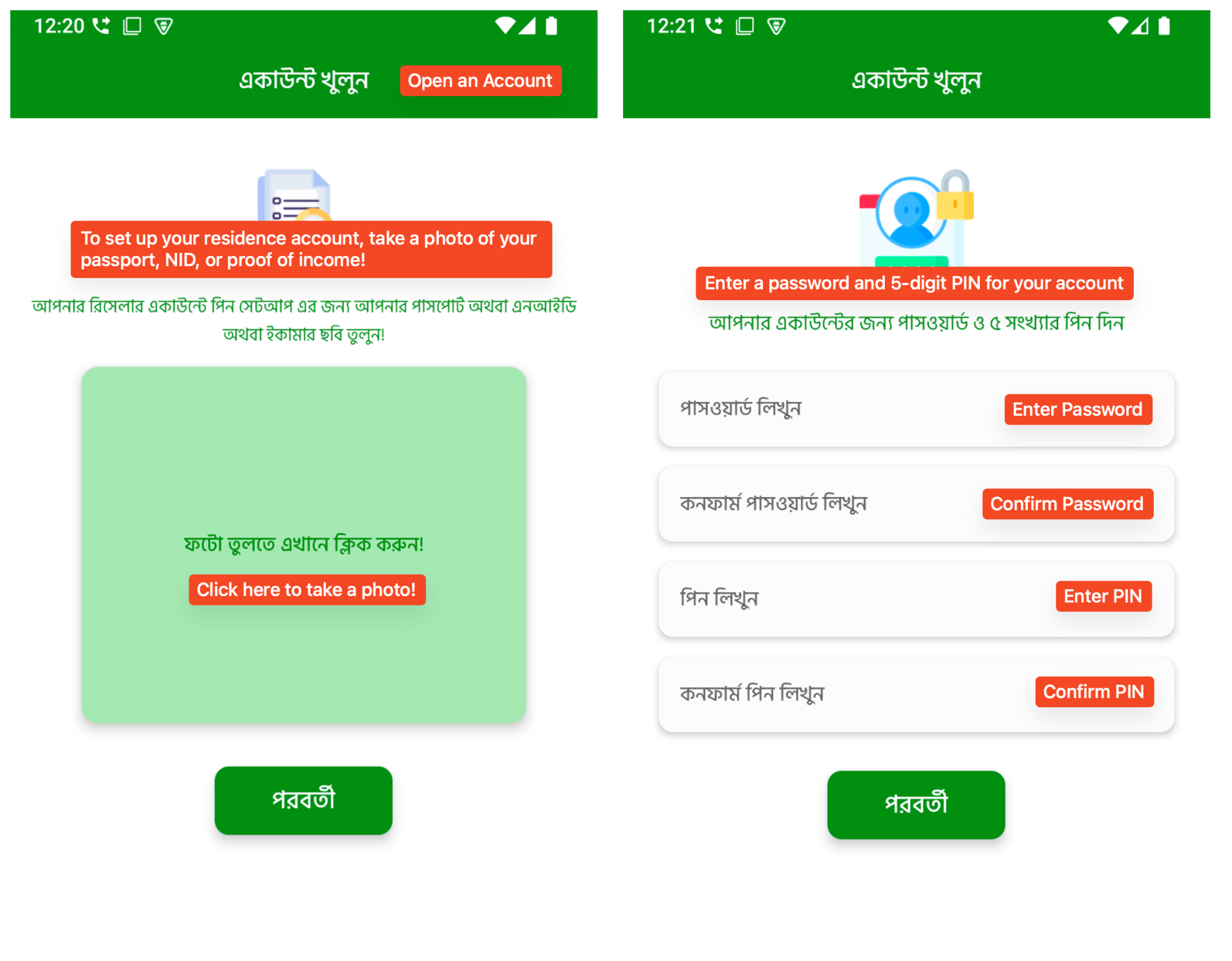
Figure 6. Multi-step registration flow (2)
After completing the registration process, users are taken to a fully designed dashboard. The interface mimics a real financial or remittance app, complete with icons for money transfer, bill payment, mobile banking, and even customer support features.

Figure 7. The fake TapTap Send app’s main dashboard
The malware includes multiple fake transaction interfaces. These screens simulate mobile money transfers, bill payments, and bank transfers using logos from real services. Although no actual transaction is performed, the app collects all entered information such as phone numbers, account details, PINs, and payment amounts. This data is then transmitted to the C2 server.
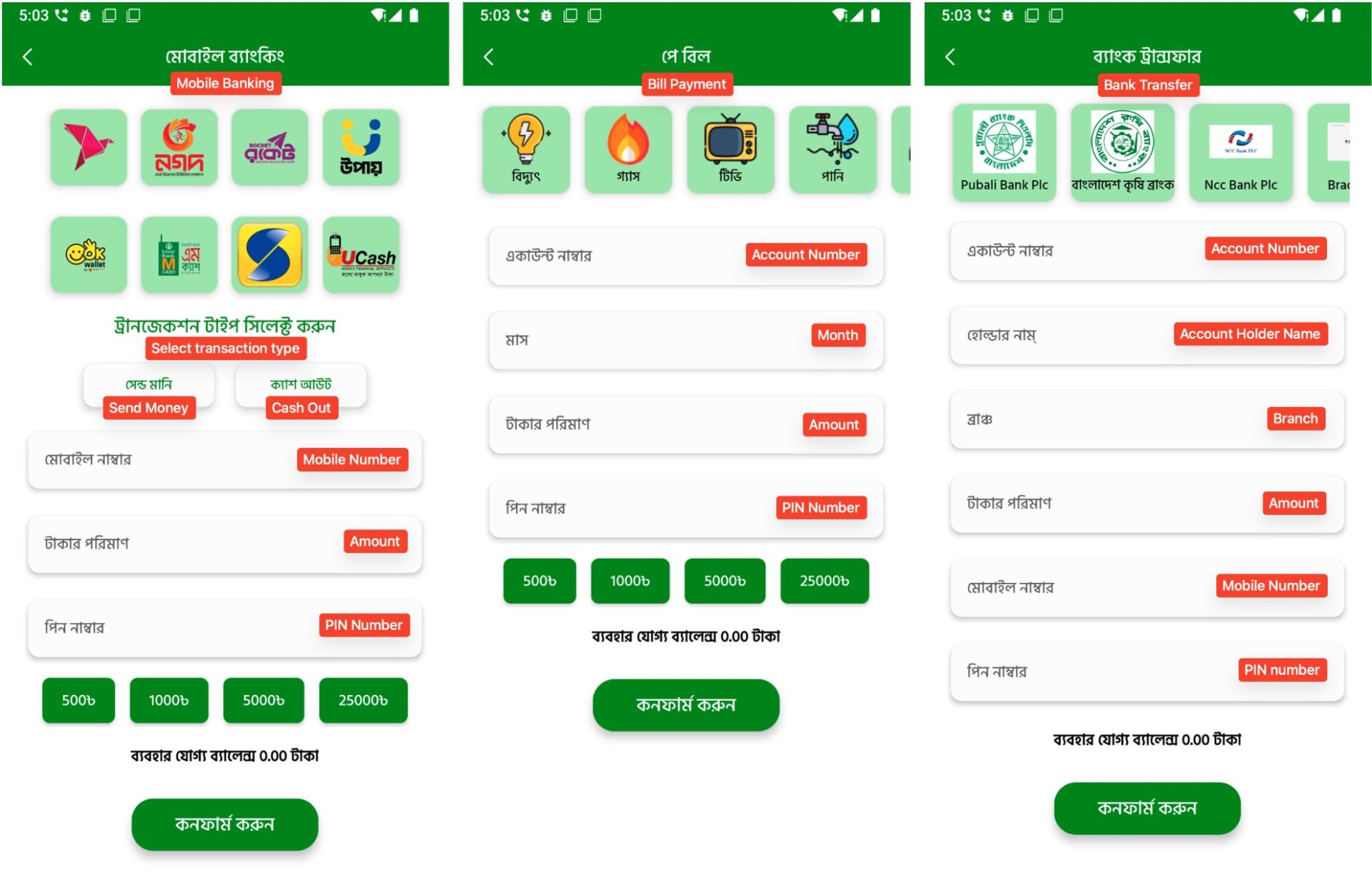
Figure 8. Fake transaction screens that imitate real financial services
C2 Server and Data Exfiltration
All the information collected by the fake app, including credentials, contact details, and photo IDs, is stored on the C2 server. However, the server lacks basic security settings. Directory listing is enabled, which means anyone can access the uploaded files without authentication. During our investigation, we found that one of the C2 domains contained 297 image files. These files appear to be photo IDs uploaded by users during the registration process.

Figure 9. Publicly accessible directory listing on the C2 server
These ID images include highly sensitive personal information and are publicly accessible. If downloaded or misused, they could pose a serious privacy and identity theft risk.

Figure 10. Example of a sensitive photo ID image uploaded during app registration
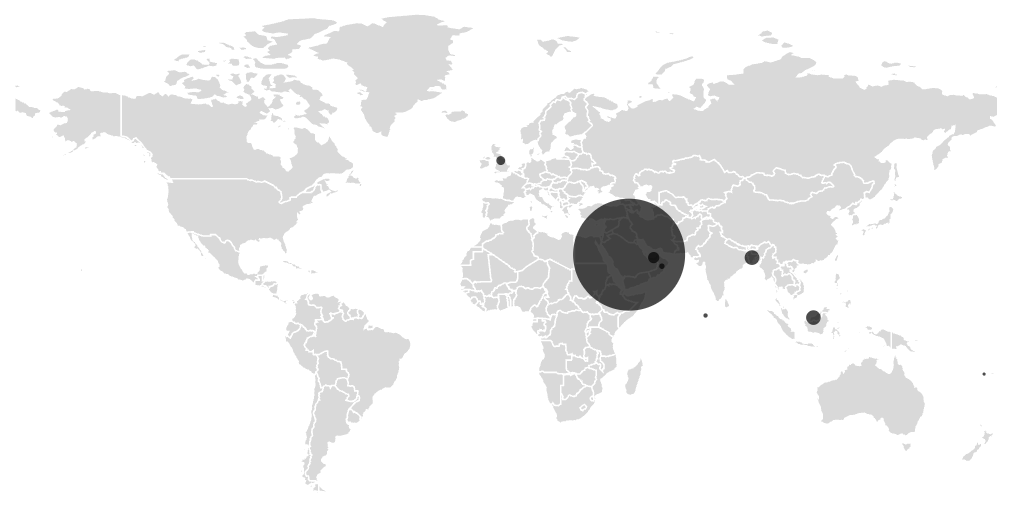
Figure 11. Geographic distribution of infected devices
As expected, telemetry shows activity in countries with large Bangladeshi populations abroad, such as Saudi Arabia, Malaysia, Bangladesh, and the United Arab Emirates. This aligns with the app’s targeting of Bengali-speaking users through culturally familiar language and visuals. The campaign remains active, with new phishing domains and variants continuing to appear. Given the evolving nature of this threat and its use of trusted platforms like Facebook to distribute malicious content, users should stay cautious when encountering financial service promotions through social media or unknown websites. We recommend downloading apps only from trusted sources such as Google Play, avoiding links shared via social media, and being extra careful when asked to provide personal or banking information. Using mobile security software that can detect and block these threats is also strongly advised.
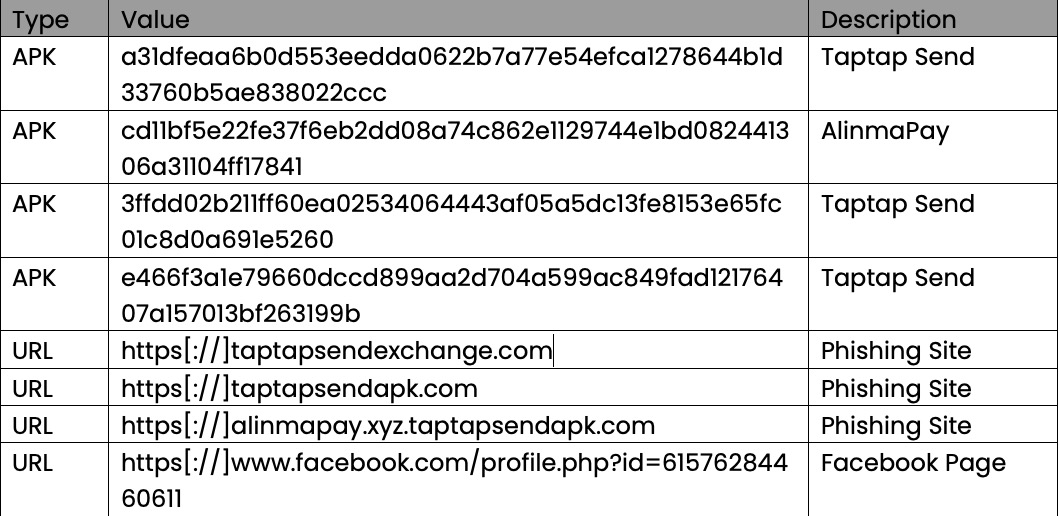
Indicators of Compromise (IOCs)