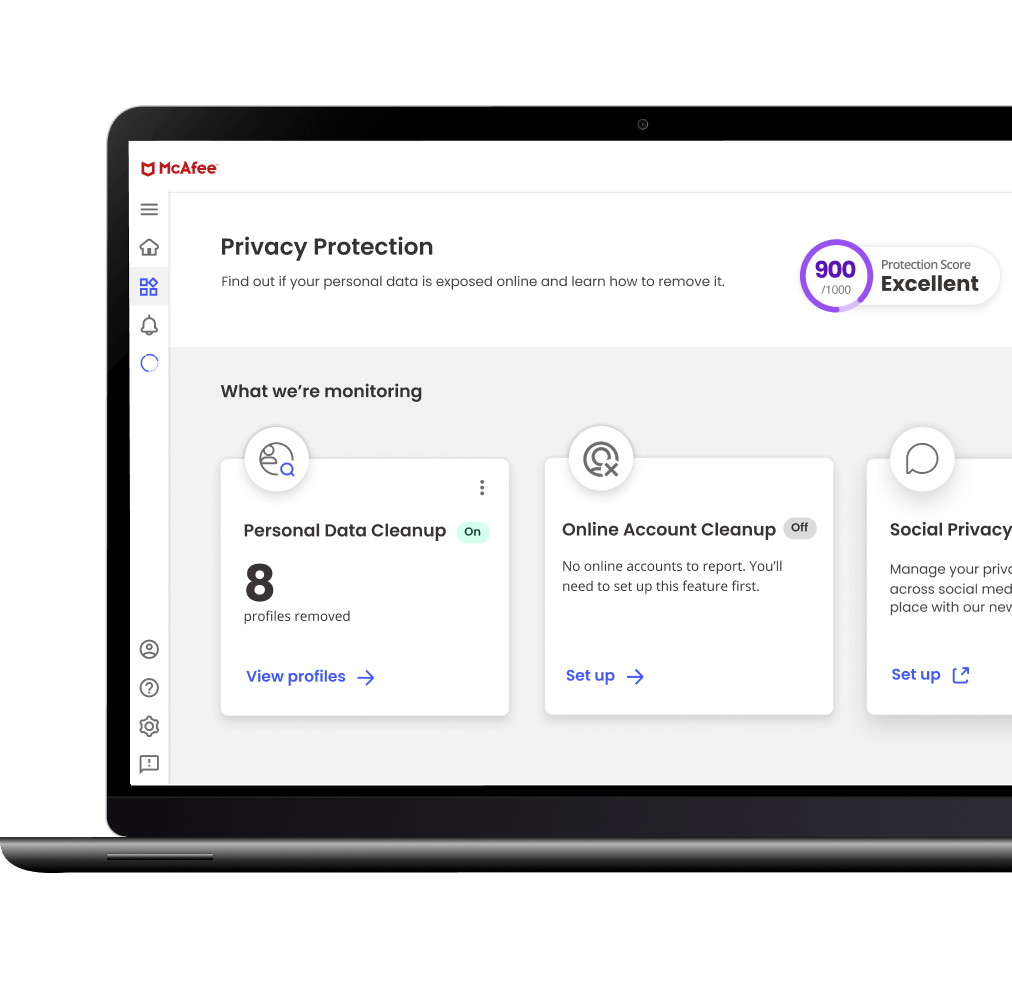
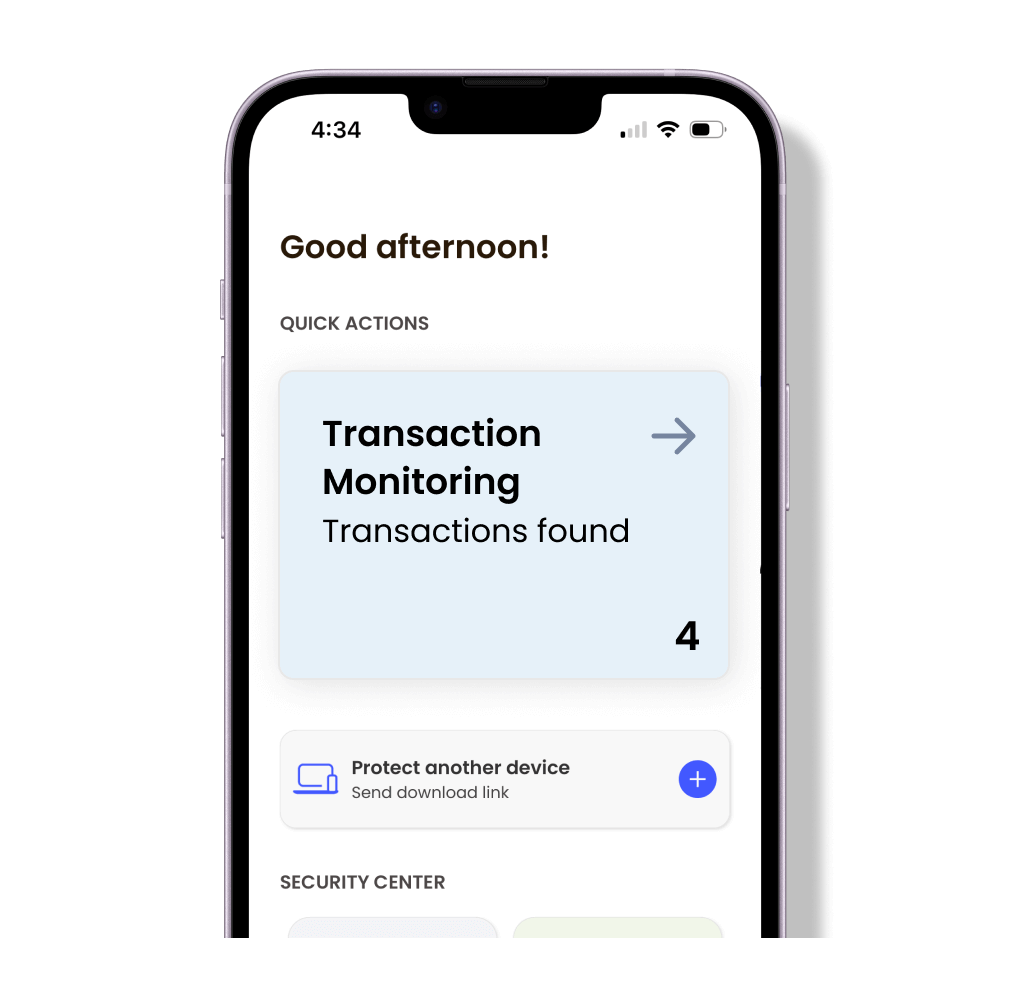
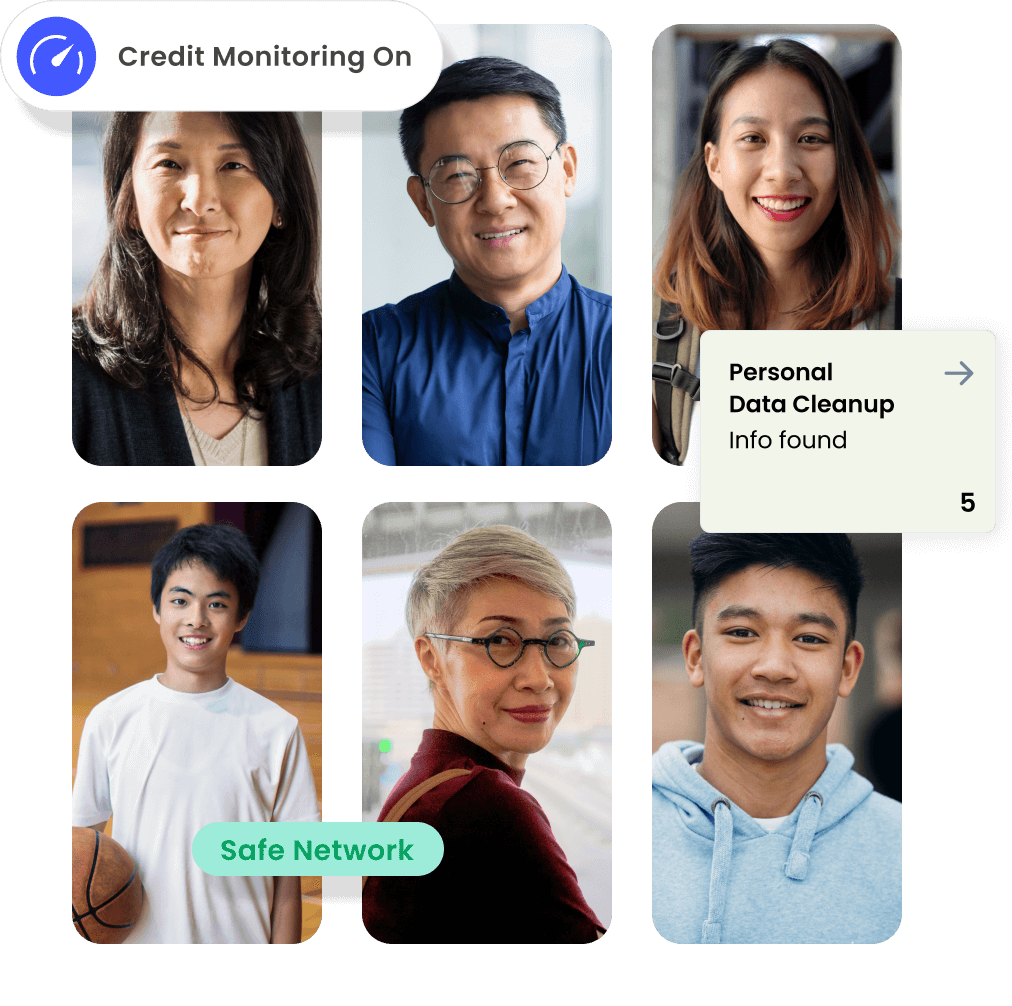
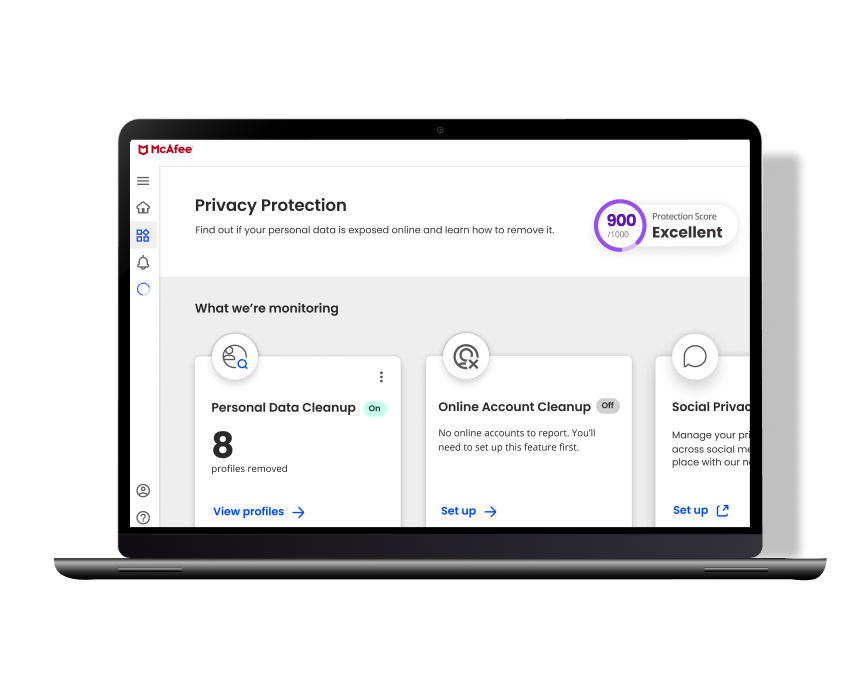
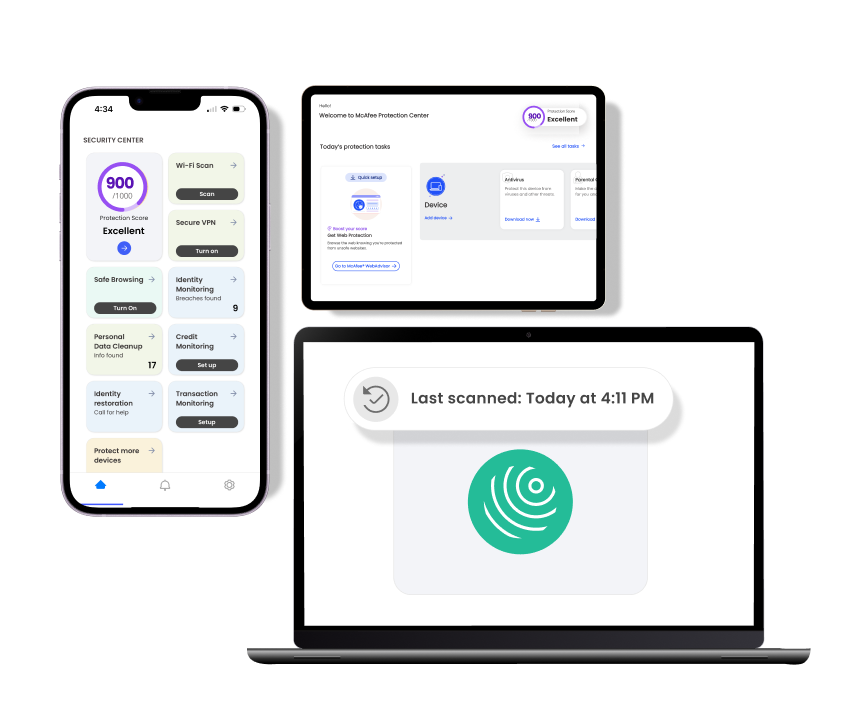
Find out instantly if your identity has been exposed
We’ll scan to see if your email has been compromised in a data breach.
All-In-One Protection
Complete privacy, identity and device protection for individuals.
Complete privacy, identity and device protection for up to 6 family members.
Basic device and identity protection for individuals
Other Products & Services
Free Tools & Downloads
Get the app
Keep Me Private Online
Safeguard My Identity
Protect My Devices
Protect My Family
All-In-One Protection
Complete privacy, identity and device protection for individuals.
Complete privacy, identity and device protection for up to 6 family members.
McAfee Total Protection Plans
Basic device and identity protection for individuals
Other Products & Services
Free Tools & Downloads
Get the app
Keep Me Private Online
Safeguard My Identity
Identity Theft Coverage & Restoration
Protect My Devices
Protect My Family
Our Company
Our Efforts
Join Us
ASIA PACIFIC
EUROPE
This site in other countries/regions:
ASIA PACIFIC
EUROPE



















We’ll scan to see if your email has been compromised in a data breach.